
Articles
Explore Topics

HSM vs KMS: The CISO’s Guide to Strategic Key Management
Real-world experiences from the cryptographic trenches When a blockchain wallet provider detected anomalous activity in

Data Masking Tools Gartner (Updated 2026): Comparing top-rated data masking tools
Choosing the right data masking tools can be overwhelming with many options available in the

What Is PKIaaS? PKI as a Service for Machine Identity Security
Public Key Infrastructure (PKI) is no longer a niche security function buried inside IT, it

SSH Key Management vs. SSH Certificates: The Definitive Guide for Enterprise Zero Trust
The Secure Shell (SSH) protocol is a foundational technology for secure remote access, system administration,

What is PKI in Cybersecurity? The Complete Guide for Cloud, Hybrid, and On Prem Teams
Public Key Infrastructure (PKI) is a core security framework that enables trusted digital identities and

5 Step Approach to PKI + CLM Solution Selection
After years of buildup and preparation, 2026 will be a decisive inflection point for machine

API Access Control: Optimizing your API Security
In the digital transformation era, APIs have become the glue that holds modern tech stacks

Quebec Law 25 / loi 25: Data Compliance Considerations and What You Need to Know
It has now been one year since Quebec’s Law 25 (formerly Bill 64) came fully

Building a Secure Test Data Management Strategy in Financial Services
Financial institutions do not need a reminder that testing with sensitive data is a balancing

The Ultimate Guide to Keyfactor EJBCA
EJBCA (Enterprise JavaBeans Certificate Authority) is a mature, open-source PKI (Public Key Infrastructure) platform originally

SQL Server Data Management Challenges
Microsoft SQL Server remains one of the most widely deployed relational database platforms in enterprise

What is Data Masking? Techniques, Types, and Best Practices
As data becomes increasingly important for organizations, the balance between usability and . However, with

The Ultimate Guide to Test Data Management
In 2024, over 22% of data breaches involved compromised data in development, test, or staging

How to Implement GDPR Data Masking Without Sacrificing Data Usability
If you work with customer data, ensuring GDPR compliance by masking all your PII is

Data Masking Challenges in Complex Data Environments for DBAs
As a database administrator, your responsibilities extend beyond maintaining system uptime and optimizing queries. You’re

What is a Cloud HSM? Understanding Cloud Hardware Security Module (HSM) Advantages Compared with On-Premises HSMs
Protecting cryptographic keys is a core security necessity. Hardware Security Modules (HSMs) are specialized, tamper-resistant

Understanding Data Protection in Healthcare: How to Find, Manage and Protect PHI Data
What Is Classified as Protected Health Information (PHI) or Sensitive Data in Healthcare? Protected Health

Guide to Synthetic Data Generation: Tool for Secure Testing and AI
The rapidly evolving landscape of data privacy regulations, coupled with the increasing demands of AI/ML

Guide to PCI DSS 4.0 Compliance: PCI Data Masking and Tokenization
The Payment Card Industry Data Security Standard (PCI DSS) 4.0 marks the most significant evolution
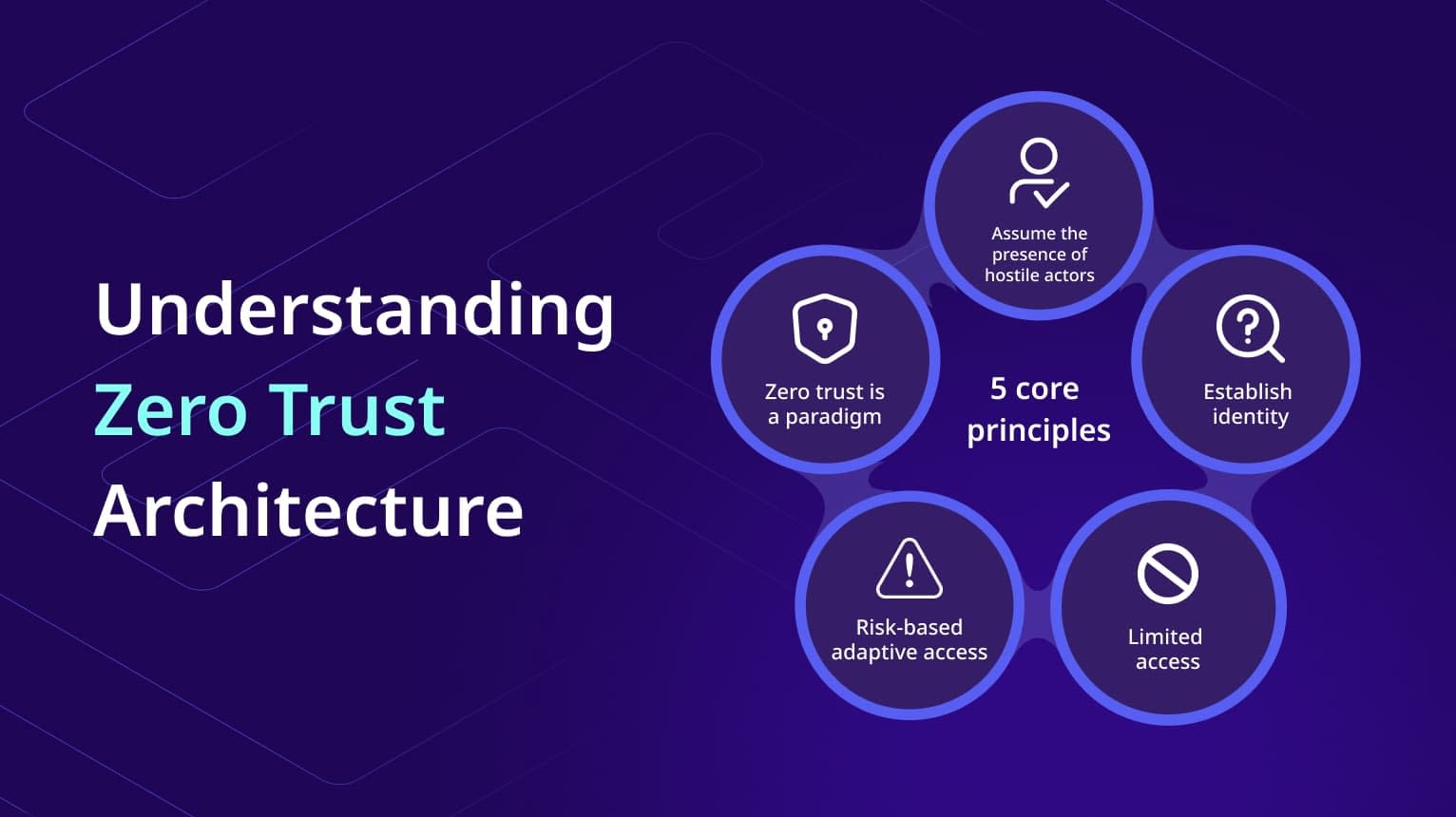
Understanding Zero Trust Architecture: From Establishing Identity to Least Privilege
Over the last few years, the approach to cybersecurity has undergone a fundamental transformation. The

The Shift to 47-Day Certificates: Shorter SSL/TLS Cert Windows are a Defining Moment for Cybersecurity
The operational landscape for managing the Public Key Infrastructure (PKI) that supports TLS is undergoing

Public Key Infrastructure (PKI) Software: Buyer’s Guide
Choosing a Public Key Infrastructure (PKI) solution isn’t just about comparing features. Security and IT

IoT PKI and Certificate Management: Guide to Securing IoT and OT Identities
The Internet of Things (IoT) and Operational Technology (OT) have revolutionized industries by connecting billions

Data Masking for the Banking Industry: Key Considerations for Financial Institutions
The financial industry is built on trust, and a crucial component of that trust is

Understanding Passkeys and Hardware Tokens: Building phishing-resistant authentication
Phishing attacks evolved far beyond the poorly written email scams they were known for. Cybercriminals

CISO Challenges for 2025: Overcoming Cybersecurity Complexities
As organizations recognize the immense value and criticality of your data and systems, cybersecurity has

How to Choose the Right Test Data Management Tools
In today’s fast-paced, compliance-focused world, choosing the right test data management (TDM) tools is vital

Post-Quantum Cryptography: The Implications of Google’s Willow and Other Quantum Computers for Cybersecurity
Quantum computing was long considered to be part of a distant future. However, it is

Apple 45-Day Certs: Implications for Certificate Lifecycle Management
Remember when we were bracing ourselves for 90-day certificates? Google’s proposed move to 90-day TLS

5 Powerful Integrations with Thales HSMs (Hardware Security Modules)
Organizations managing sensitive data know that securing encryption keys and ensuring regulatory compliance are non-negotiable.

Navigating Certificate Lifecycle Management
Managing digital certificates might sound simple, but for most organizations, it’s anything but not simple.
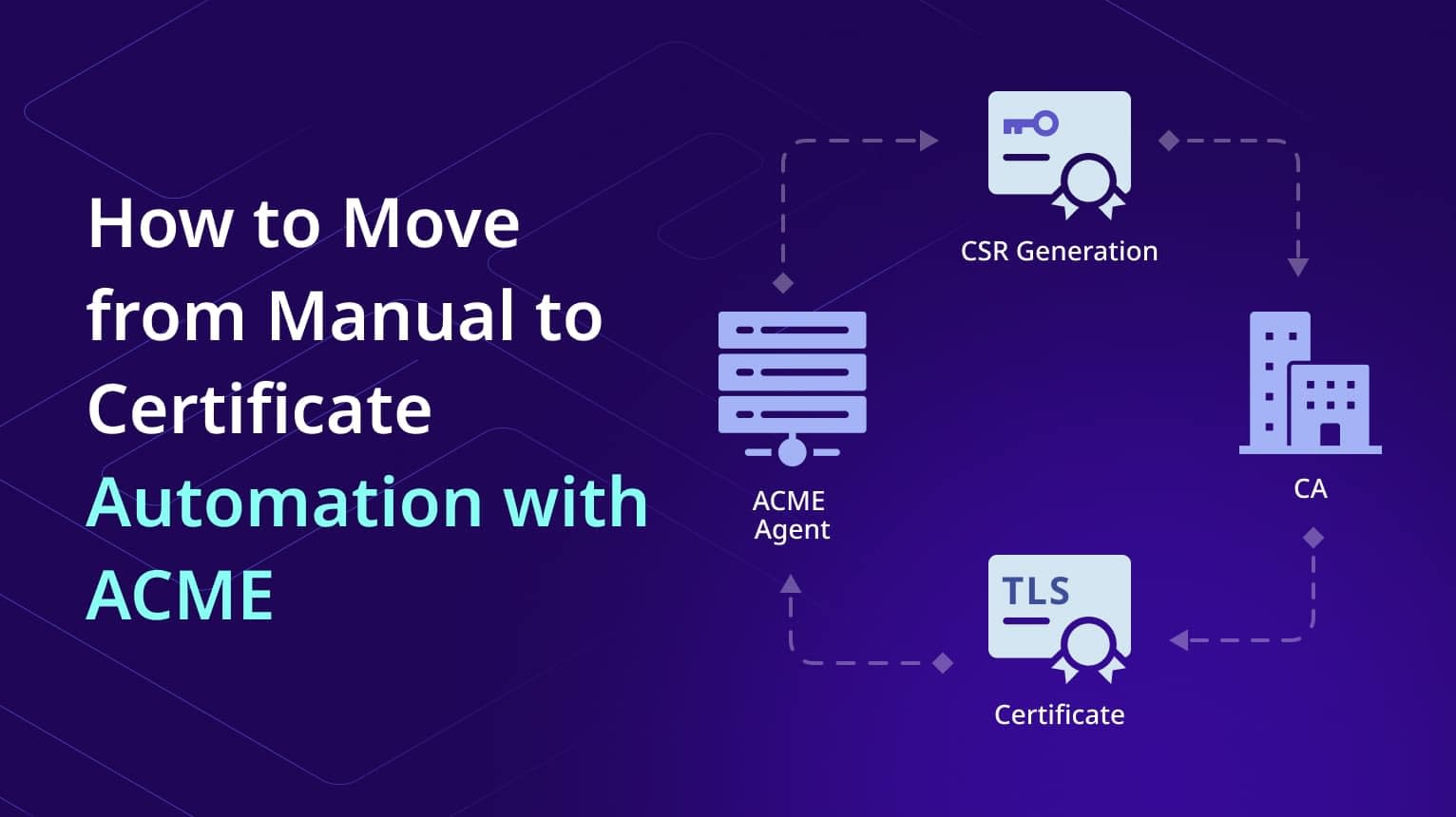
How to Move from Manual to Certificate Automation with ACME
For IT teams, managing certificates can feel like a relentless cycle of tracking expiration dates,

Sensitive Data Discovery for Enterprises: Turning Data Chaos into Compliance
In today’s data-driven landscape, sensitive information—like PII (Personally Identifiable Information), PHI (Protected Health Information), and

Test Data Management Best Practices For Sensitive Data
Handling large volumes of sensitive data in testing environments is challenging. You need to protect

Data Masking Challenges: Overcoming Complexities in Multi-Database Environments
In today’s data-driven landscape, protecting sensitive information while keeping data usable is a growing challenge

Test Data Management & Compliance Challenges For On-Prem Environments
Managing test data in on-prem environments can feel like an uphill battle. As cloud adoption

Choosing the Best Data Anonymization Tools: A Guide for Secure DevOps
When handling sensitive data in today’s regulatory landscape, especially in industries like finance, healthcare, and

PII masking : How to Anonymize Sensitive Data with Accuracy and Speed?
Protecting sensitive data isn’t just a technical challenge—it’s a balancing act. PII masking is critical

Managing Certificate Chaos After Google’s Entrust Distrust
When Google decided to stop trusting new TLS certificates from Entrust, it didn’t just create
Synthetic vs. Realistic Data for Gen AI & LLM?
How are you training your generative AI models? In AI and machine learning (AI-ML), the

7 features to look for in a PII Data Discovery Software
If you’ve ever tried to manually scan, find, and de-identify sensitive data like PII and

The Ultimate Guide To Data Masking
In today’s data-driven world, keeping sensitive information safe is more important than ever. Data breaches
Oracle Data Masking: Oracle Enterprise vs. Alternatives
Oracle Database Overview For decades, Oracle has been a leader in the database management system

Data Breach Statistics [2025] : Penalties and Fines for Major Regulations
In today’s data-driven world, data breaches are one of the most significant threats facing organizations,

The CJIS Compliance Deadline is Fast Approaching | Is your state / local government ready?
The deadline for CJIS compliance is rapidly approaching – it is mandated that all entities
Rebuilding Public Key Infrastructure | Why are 98% of organizations unhappy with their PKI?
Keyfactor’s annual PKI & Digital Trust Report for 2024 contained a bombshell finding – 98%

PIPEDA Compliance with Accutive Data Discovery and Masking: Understanding and protecting your Canadian sensitive data
What is PIPEDA, Canada’s Personal Information Protection and Electronic Documents Act? PIPEDA, or the Personal

CCPA Compliance with Accutive Data Discovery and Masking: Understanding and protecting your sensitive data
What is the CCPA, the California Consumer Privacy Act? CCPA, or the California Consumer Privacy
Solving Kubernetes Security Complexities with Machine Identity Management
What is Kubernetes? A foundational cloud native technology If you’re in the IT world, you’ve likely

Google’s Push for 90-Day SSL/TLS Certificates: Is 90-day cert expiry coming?
The world of digital certificates is about to change drastically. Driven by Google and other

Securing public safety organizations with HID’s CJIS-certified MFA
In the law enforcement and public safety space, securing access to sensitive information is paramount.

Navigating your Certificate Landscape: The Role of Machine Identity Management (MIM) and Certificate Lifecycle Management (CLM)
Managing your machine identities and the certificates that authenticate them are a critical component of

Guide to Digital Authentication: Human and Machine Identities
As technology advances and the digital landscape becomes increasingly sophisticated, it makes our lives easier

Thales + Imperva: Echoes of the Transformative Impact of the Gemalto Acquisition?
The Gemalto Legacy: Setting the Stage for Transformation The acquisition of Gemalto by Thales in
Your Guide for Vormetric DSM to Thales CipherTrust Data Security Platform Migrations
The transition from Vormetric Data Security Manager (DSM) to Thales CipherTrust Data Security Platform (Thales

Migration from KeySecure to Thales CipherTrust: A Guide for your organization
The transition from KeySecure to Thales CipherTrust Data Security Platform (Thales CDSP) presents a sense

Dispelling Misconceptions: A Breakdown of PKI and CLM
When meeting with clients, we often encounter the incorrect idea that Public Key Infrastructure (PKI)

ServiceNow Certificate Management: Efficient, Integrated Cert Management
The Need for Efficient Certificate Management In a world increasingly dependent on digital transactions and

Unlocking Compliance Excellence: Integrating NERC and CIP Standards into DevOps and DevSecOps
This comprehensive guide explores how adopting DevOps and DevSecOps principles can streamline compliance with NERC

End of Life for MS 2012 Server: Impacts and Necessary Upgrades
Microsoft announcement regarding the end-of-life (EOL) for Windows Server 2012 has been a wake-up call

ANMSoft Enhances Data Management Capabilities with Accutive Security Data Discovery and Masking [Press Release]
ANMSoft Technologies Pvt Ltd, a premier technology solutions provider, has integrated Accutive Security’s Data Discovery

The Future of SSL/TLS Certificates: Navigating the Shift to 90-Day Validity
The world of digital certificates is rapidly evolving, as evidenced by the Google Chromium Project’srecent

CA/B Forum Code Signing Upcoming Requirements Changes Begin in June: Let Accutive Security help!
From June 1, 2023, the Certificate Authority/Browser (CA/B) Forum is mandating a significant change to

9 Major Data Privacy Regulations from Around the World: A Comprehensive Guide
In today’s digital age, data privacy has become a major concern for individuals and organizations

The Importance of Retaining a Cybersecurity Company: Accutive Security
Cybersecurity is a growing concern for businesses of all sizes, with the frequency and sophistication