If you work with customer data, ensuring GDPR compliance by masking all your PII is crucial. But GDPR data masking is not just about meeting regulatory requirements; it involves navigating complex challenges to both protect data and maintain its usability. GDPR mandates that PII must be protected through techniques like anonymization and pseudonymization, which involve replacing real data with non-identifiable alternatives.
While this process might sound simple, but for enterprises that have customer data sprawled across multiple environments and business applications, GDPR data masking is a nightmare. The primary challenge is to mask data without compromising its usefulness. If the data becomes too altered, it can render it ineffective for essential tasks such as QA, testing, and development.
Striking the right balance between data protection and functionality is essential. In this guide, we will delve into the specific challenges of GDPR data masking and discuss practical strategies to ensure compliance without sacrificing data functionality.
What are the GDPR Data Regulations?
The General Data Protection Regulation (GDPR) (Regulation (EU) 2016/679) sets out strict rules on how personal data must be collected, processed, stored, and protected. It applies to any organization, within or outside the EU, that processes personal data of individuals in the EU. Crucially, organizations in the U.S., Canada and other non-European countries that do business with the EU likely have obligations under GDPR. This broad scope is part of the reason why GDPR is becoming a global data privacy standard that leading organizations benchmark their data protection policies and tools against.
Key legal obligations of GDPR include:
See GDPR Compliance In Action
With the growing need for data for DevOps, AI model training and analytics, many organizations have used production data outside of secure environments. In response, GDPR enforcement is increasingly targeting how data is handled outside production systems, especially in DevOps, analytics, and AI workflows:
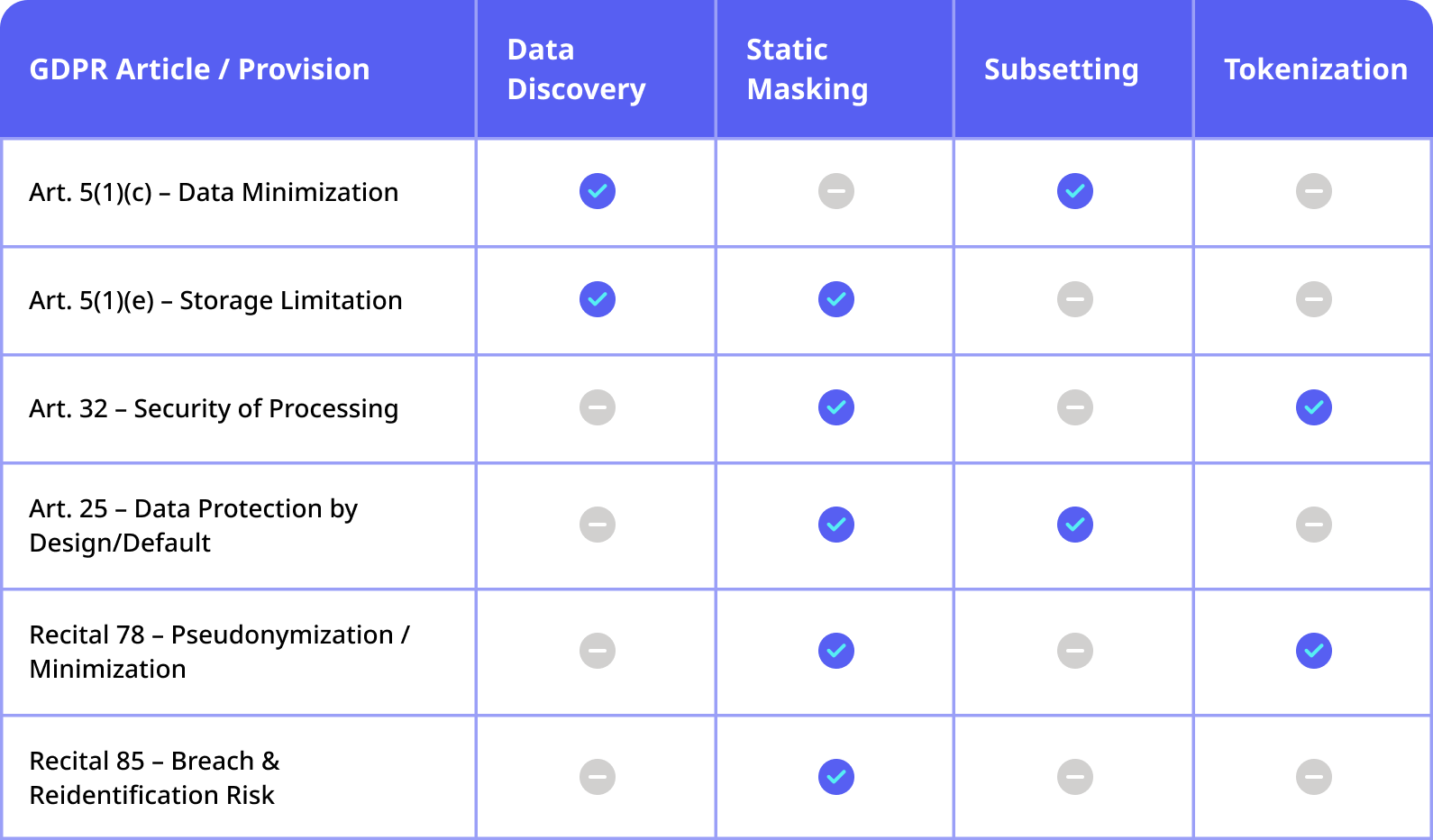
- EDPB Guidance (2024) clarified that unmasked production data in dev/test environments is a violation of Article 5(1)(a) (lawfulness, fairness, transparency) unless pseudonymized or anonymized.
- The EU AI Act (now in force) reinforces requirements for Article 25 compliance when using personal data in machine learning pipelines—boosting demand for synthetic data and masking technologies.
- Regulators are prioritizing Article 30 (Records of Processing Activities), requiring organizations to show where data resides and how it is protected across environments.
- Several high-profile fines in 2024–2025 (ranging from €8M to €22M) have targeted organizations for excessive retention (Article 5(1)(e)), poor access controls (Article 32), and weak pseudonymization.
GDPR is designed to prevent data sprawl and ensure that organizations know and protect all their sensitive data. GDPR emphasizes the importance of data protection by design and by default, which includes the use of methods like anonymization and pseudonymization to safeguard sensitive information. In practical terms, this means organizations are expected to implement data masking techniques that reduce the risk of exposing real identities in non-production environments such as development, testing, or analytics.
Organizations that fail to comply face steep penalties—up to €20 million or 4% of annual global turnover—making robust data protection not just a legal obligation but a business-critical priority.
How Data Masking Helps Ensure GDPR Compliance
Data masking plays a critical role in helping organizations achieve GDPR compliance by protecting PII while preserving its utility for operational and analytical purposes. Under GDPR, it’s not enough to simply restrict access to raw data; organizations must actively minimize the risk of exposure by transforming data in such a way that individuals cannot be identified—even indirectly.
Here’s how data masking contributes to GDPR compliance:
- Supports Anonymization and Pseudonymization: GDPR recognizes anonymized and pseudonymized data as safer alternatives to raw PII. Data masking allows organizations to render personal data unidentifiable—either permanently (anonymization) or reversibly under strict controls (pseudonymization).
- Reduces Exposure in Non-Production Environments: Development, testing, and QA environments often use real data for realism. Data masking enables these teams to work with realistic, yet de-identified, datasets—drastically reducing the risk of unauthorized access or leaks.
- Enables Principle of Least Privilege: By masking data, organizations can give teams access to the information they need—without exposing full PII—helping enforce the GDPR principle of data minimization.
- Enhances Breach Resilience: In the event of a breach, masked data dramatically lowers the risk of GDPR penalties, since compromised information does not directly identify individuals.
Ultimately, data masking is not just a best practice—it’s a strategic enabler of GDPR compliance. When implemented correctly, it helps organizations protect customer privacy, reduce regulatory risk, and continue leveraging their data for innovation and business growth.
Start with a complimentary GDPR data compliance assessment
The Challenges of GDPR Data Masking
At first glance, GDPR data masking might seem simple—just mask the sensitive data, and you’re done. But in reality, it’s much more complex. Data doesn’t stay still; it’s always changing as new information is added and linked, which brings hidden challenges. If you don’t address these challenges, you risk compliance issues and operational inefficiencies.
Here are some key challenges you need to tackle to ensure compliance without compromising data usability:
- Contextual Data Sensitivity:
Data sensitivity isn’t always straightforward. For example, a postal code might seem harmless on its own but becomes sensitive when combined with other personal identifiers. Effective GDPR data masking strategies must account for these contextual nuances to ensure comprehensive data protection. - Managing Performance Impact:
Real-time masking might seem appealing, but it can strain system resources. A more effective approach involves static data masking that you can schedule, allowing you to mask data without putting undue pressure on your systems. Even with static masking, maintaining high performance is crucial to avoid disruptions. - Need for Customizable Masking :
Different data types and contexts may require tailored masking approaches. Customizable masking solutions are needed to address specific data protection needs and ensure that the masked data remains relevant and functional for various use cases. - Balancing Granularity and Efficiency:
Finding the right level of data protection is crucial. Encrypting or scrambling data can make it unusable for legitimate purposes, while inadequate protection risks exposing sensitive information. Striking the right balance is essential to ensure both security and functionality. - Consistency Across Multi-Cloud and Hybrid Environments:
As data spreads across various environments, applying consistent GDPR masking policies becomes increasingly complex. Ensuring uniform compliance and usability across all platforms isn’t just challenging—it’s essential.
ADM: Advanced Data Masking Platform for GDPR Data Masking
In today’s dynamic and interconnected data landscapes, GDPR data masking requires more than basic solutions—it demands tailored strategies that ensure your data remains usable and secure. Here’s how you can implement advanced masking techniques that address the complexities of modern data environments:
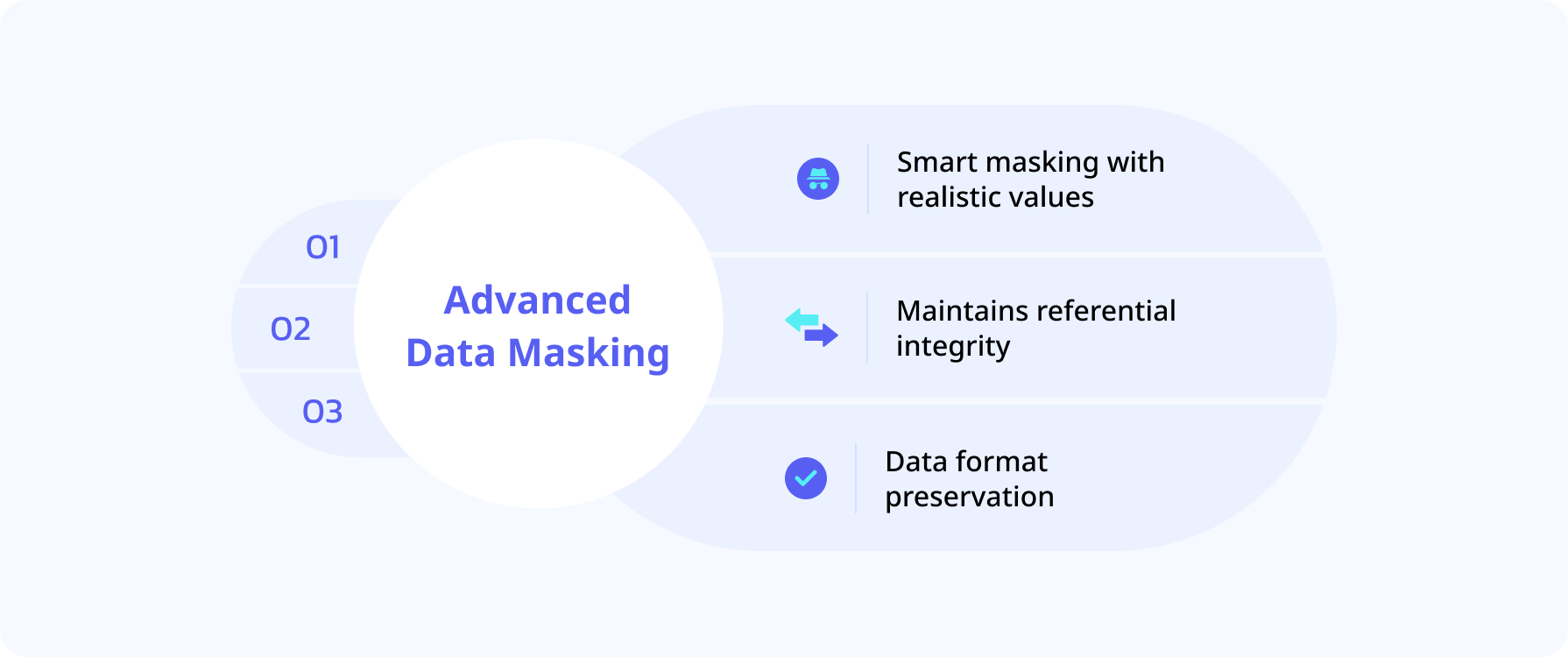
- Smart Masking with Realistic Values:
Simply masking data isn’t enough if the masked values don’t make sense in your operational context. Smart masking replaces sensitive data with realistic, yet fictional, values that blend seamlessly into your datasets. For example, instead of masking a customer’s address with random characters, smart masking might replace it with a believable (though not real) address. This approach ensures that your data remains useful for testing, analysis, and daily tasks while still protecting sensitive information. - Data Format Preservation:
Retaining the original format of the masked data is crucial for functionality. Format-preserving encryption (FPE) allows you to mask data without altering its structure. For instance, a masked credit card number should still look like a valid credit card number and pass the digit check, even though it’s no longer real. This approach ensures that your masked data can be processed and used within your systems without causing errors, maintaining both readability and functionality. - Maintains Referential Integrity:
In relational databases, maintaining relationships between data points after masking is critical. Referential integrity ensures that data links, such as foreign keys connecting different tables, remain intact even after masking. This prevents issues like broken relationships or inconsistencies across databases, which can lead to unusable data. By implementing referential integrity in your GDPR data masking strategy, you ensure that your databases continue to function as intended, even with masked data.
Conclusion: Moving to Automated GDPR Data Masking with ADM
Too often, organizations see GDPR compliance as a trade-off: secure data or usable data, but not both. This mindset leads to rigid, one-size-fits-all masking strategies that don’t address the specific needs of different data environments. But it doesn’t have to be this way.
By moving beyond manual techniques and embracing automated tools tailored to your organization’s unique data landscape, you can meet GDPR requirements while keeping your data fully usable. ADM’s Discovery and Masking solution provides automated masking that protects your data without compromising performance or usability, even in the most complex environments.
When you understand and address the specific challenges of your data environment—whether it’s managing dynamic data, preserving relationships, or ensuring system performance—you can achieve GDPR compliance while maintaining full functionality. Automated masking tools help you keep your data compliant and operational.












Comment