Articles
Explore Topics

Data Masking Challenges in Complex Data Environments for DBAs
As a database administrator, your responsibilities extend beyond maintaining system uptime and optimizing queries. You’re

What is a Cloud HSM? Understanding Cloud Hardware Security Module (HSM) Advantages Compared with On-Premises HSMs
Protecting cryptographic keys is a core security necessity. Hardware Security Modules (HSMs) are specialized, tamper-resistant

Data Masking Tools Gartner (Updated 2025): Comparing top-rated data masking tools
Choosing the right data masking tools can be overwhelming with many options available in the

Understanding Data Protection in Healthcare: How to Find, Manage and Protect PHI Data
What Is Classified as Protected Health Information (PHI) or Sensitive Data in Healthcare? Protected Health

Guide to Synthetic Data Generation: Tool for Secure Testing and AI
The rapidly evolving landscape of data privacy regulations, coupled with the increasing demands of AI/ML

Guide to PCI DSS 4.0 Compliance: PCI Data Masking and Tokenization
The Payment Card Industry Data Security Standard (PCI DSS) 4.0 marks the most significant evolution
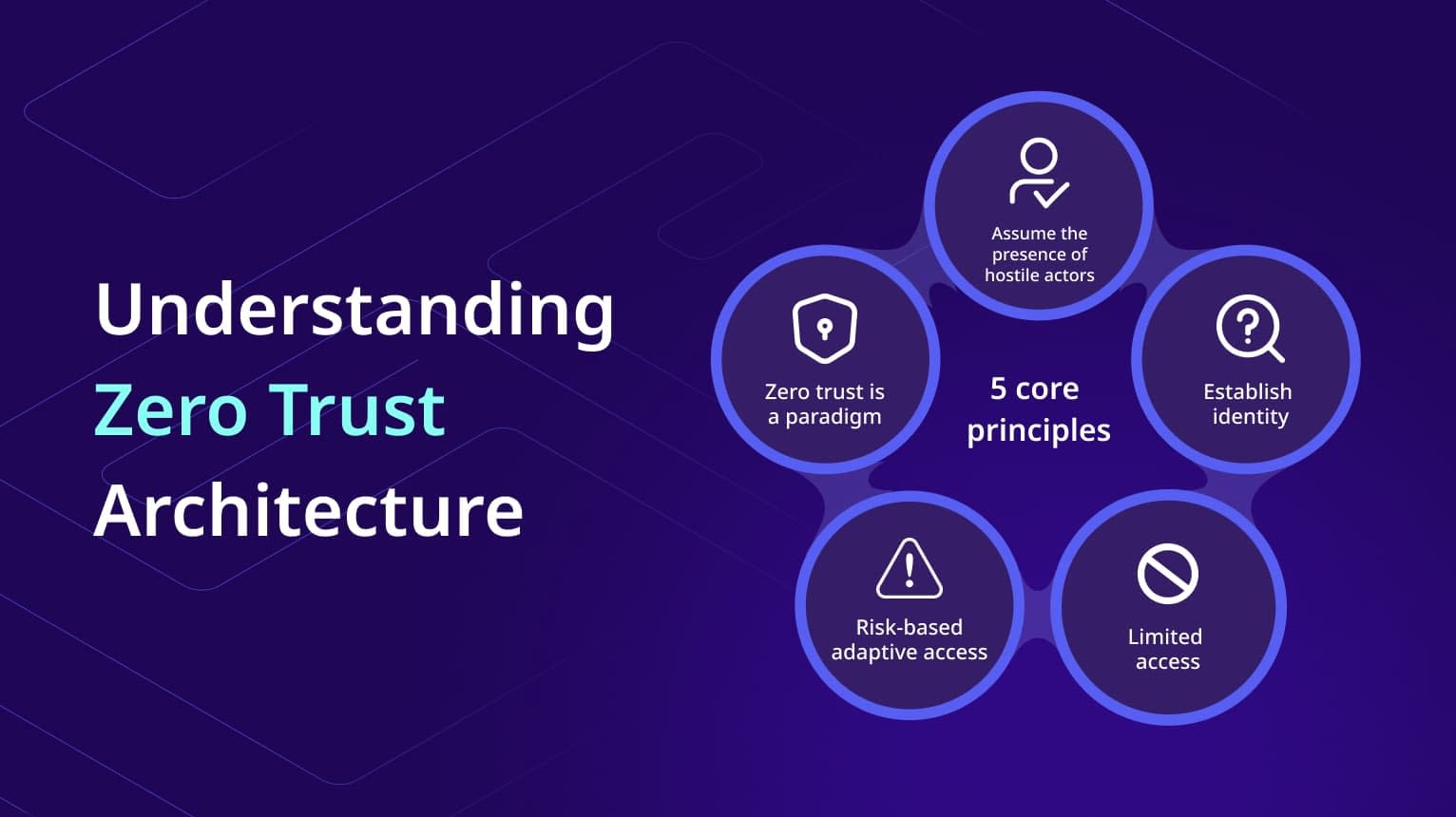
Understanding Zero Trust Architecture: From Establishing Identity to Least Privilege
Over the last few years, the approach to cybersecurity has undergone a fundamental transformation. The

The Shift to 47-Day Certificates: Shorter SSL/TLS Cert Windows are a Defining Moment for Cybersecurity
The operational landscape for managing the Public Key Infrastructure (PKI) that supports TLS is undergoing

Public Key Infrastructure (PKI) Software: Buyer’s Guide
Choosing a Public Key Infrastructure (PKI) solution isn’t just about comparing features. Security and IT

IoT PKI and Certificate Management: Guide to Securing IoT and OT Identities
The Internet of Things (IoT) and Operational Technology (OT) have revolutionized industries by connecting billions


