After years of buildup and preparation, 2026 will be a decisive inflection point for machine identity security, cryptographic operations, and enterprise security posture.
Certificate Lifecycle Management (CLM) and Public Key Infrastructure (PKI) have completed their evolution from “nice-to-have” tools, often adopted by organizations managing very large certificate volumes, into mission-critical platforms required by all enterprises to maintain security, availability, and regulatory compliance.
This shift is being driven by an industry-wide changes that materially alter how certificates must be governed, automated, and operated.
The Beginning of the 47-Day Certificate Transition
On March 15, 2026, the first phase of the transition toward 47-day certificates begins, with a halving of TLS certificate lifecycles to just 200 days. This is the first significant reduction in nearly six years and represents a fundamental shift for certificate operations.
The operational implications are immediate and unavoidable:
- Certificate renewal and rotation volumes effectively double
- Manual processes no longer scale, and are often not viable
- Gaps in certificate inventory, ownership, and automation are exposed
- The likelihood of service outages due to expired certificates increases
For organizations that have historically managed certificates as a background operational task, this change forces a reassessment. Certificate management is no longer an operational hygiene issue; it is a core resilience and risk-management concern.
Why Many Organizations Struggle to Find the Right CLM Solution
As certificate lifecycles shorten, many organizations are reaching out to our Center of Excellence looking to accelerate their efforts to adopt or replace their CLM platform. For many organizations, the CLM market appears increasingly complex with opaque and overlapping capabilities, and uncertainty about what they actually need.
Common challenges we hear include:
- Difficulty distinguishing foundational CLM capabilities from optional or superfluous features.
- Knowing which platforms are suitable for an automation roadmap, beginning with partial automation and eventually progressing to fully certificate lifecycle automation.
- Understanding which platforms are suitable for specialized use cases, such as managing containerized workloads and certificates for IoT and OT deployments.
- Demystifying how PKI and CLM differ from, and integrate with Certificate Authorities (CA).
Without deep PKI and cryptographic expertise, organizations often select whichever tool is more affordable that meets their immediate needs. Unfortunately, this has led many organizations to select or build solutions that lack the maturity to support long-term security and compliance objectives. Today, many of these organizations are struggling to scale up their operations to keep pace with the aggressive shift toward 47-day TLS certificates.
We recommend organizations avoid these pitfalls by undertaking by a thorough, expert-led selection process that ensures CLM and PKI buying decisions are driven by a holistic understanding of your needs.
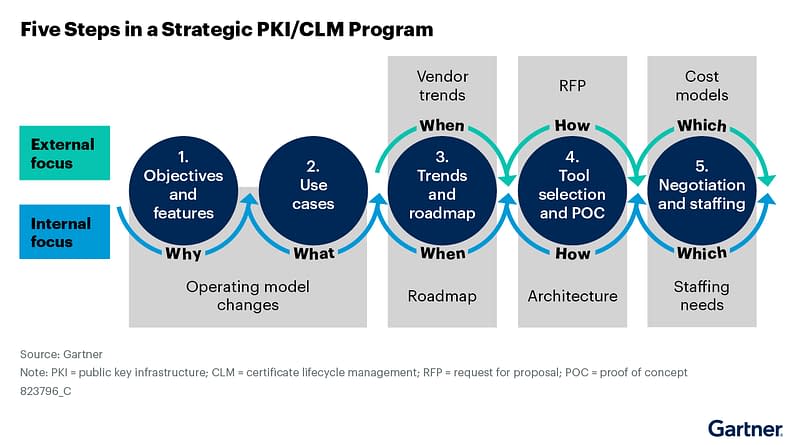
A Strategic Framework for PKI and CLM Programs
Gartner outlines a structured five-step approach for building a sustainable and scalable PKI and CLM program. This framework aligns with 5 key questions that Accutive Security uses to advise enterprise across regulated, cloud-native, and high-availability environments.
Your organization can start planning your 47-day ready PKI/CLM program with these five key questions:
1. What Objectives and Features do you need from your CLM / PKI?
A successful PKI and CLM program begins with clarity around business, risk, and operational realities. Before evaluating platforms, organizations must understand:
- Certificate volume and growth trajectory, including current inventory size, rate of issuance, and expected expansion.
- Certificate types and trust models, such as public TLS, private/internal TLS, client authentication, code signing, and device identity certificates.
- Specialized environments and use cases, including OT, IoT, containerized workloads, and non-interactive machine identities that introduce unique lifecycle and security constraints.
- Renewal cycles and operational cadence, particularly as lifetimes shorten and automation requirements increase.
- Availability and uptime dependencies tied to certificates supporting critical services.
- Regulatory, audit, and compliance obligations across jurisdictions and industries.
- Security risk tolerance and incident impact thresholds, including the blast radius of certificate-related outages.
- Long-term cryptographic strategy, including crypto-agility and post-quantum readiness.
Without alignment across these dimensions, CLM implementations tend to become reactive: focused on managing renewal events rather than enabling scalable automation, reducing enterprise risk, and improving long-term resilience.
2. What Use Cases do you need your CLM/PKI to support?
Although 47-day TLS certificates are a major driver of PKI and CLM investments, it is important that organizations do not improperly limit the scope of their platforms to TLS. While TLS is often the initial and most visible use case, it represents only a subset of the machine identity and trust requirements across the enterprise.
A mature PKI and CLM program must be designed to support a broad and evolving set of use cases, including:
- Public and private TLS certificates for external services, internal applications, and east–west traffic.
- API and service authentication, particularly in distributed and microservices-based architectures.
- DevOps and CI/CD pipelines, where certificates and keys are required for secure automation and code promotion.
- Cloud and containerized workloads, including short-lived identities in Kubernetes, service meshes, and ephemeral infrastructure.
- Machine identity for IoT and OT environments, where scale, lifecycle constraints, limited connectivity, and long-lived devices introduce unique operational challenges.
- Client authentication and mutual TLS, supporting zero trust and strong identity assurance models.
- Code signing and software integrity, increasingly critical for supply chain security and regulatory compliance.
Defining and prioritizing these use cases is essential to ensuring that the selected CLM and PKI platforms can scale, automate, and integrate across diverse environments. Although 47-day TLS certificate renewals are an immediate issue, platforms chosen solely to solve immediate TLS renewal challenges often become limiting factors as organizations expand into cloud-native, machine-to-machine, and operational technology use cases.
3. What is your PKI roadmap and how does each platform align with it?
PKI and CLM are not static technologies. They operate at the intersection of cryptographic standards, platform dependencies, and evolving security and regulatory expectations. As certificate lifecycles shorten and machine identity continues to proliferate, organizations must move away from treating CLM as a one-time deployment and instead manage it as a continuously evolving capability.
A robust PKI and CLM roadmap should account for:
- Shortening certificate lifecycles, including phased reductions in public certificate validity periods and the resulting impact on issuance, renewal, and automation requirements, as well as shortening internal certificate lifecycles for compliance and security purposes.
- Cryptographic evolution, such as algorithm deprecation, key size changes, and long-term crypto-agility to support future standards and post-quantum transitions.
- The explosion in machine identity volumes, driven by cloud adoption, microservices, containers, APIs, IoT, and OT environments.
- Integration dependencies, including identity platforms, DevOps tooling, cloud providers, service meshes, and security controls.
- Vendor and platform roadmaps, ensuring selected CLM and PKI solutions can mature alongside organizational needs rather than forcing costly re-platforming.
- Operational maturity progression, from visibility and inventory management to partial automation and ultimately fully automated, policy-driven lifecycle management.
Without a clearly defined roadmap, we find that PKI programs tend to accumulate technical debt. Short-term decisions made to address immediate certificate renewal or outage risks can introduce long-term fragility, limit automation, and constrain cryptographic agility.
Organizations that invest in a living PKI and CLM roadmap typically find themselves better positioned to absorb industry changes, such as continued shortening of certificate lifetimes, without disruption, while continuously improving security posture and operational resilience.
4. What is your selection criteria and proof of concept requirements?
Effective CLM and PKI platform selection cannot rely solely on vendor demonstrations, feature matrices, or reference architectures. Many critical capabilities—particularly those related to scale, automation, integration, and operational resilience—only become apparent when platforms are evaluated in conditions that reflect real enterprise environments.
Selection criteria should be grounded in the organization’s defined objectives, use cases, and roadmap, and should explicitly evaluate:
- Automation depth and flexibility, including policy-driven issuance, renewal, and revocation across diverse certificate types and environments
- Scalability and performance, particularly for high-volume issuance, short-lived certificates, and burst scenarios driven by automation
- Integration capabilities, including native and API-based integration with cloud platforms, DevOps pipelines, identity systems, and security tooling
- Support for diverse environments, such as hybrid infrastructure, containerized workloads, IoT, and OT deployments
- Operational visibility and governance, including inventory accuracy, ownership attribution, auditing, and reporting
- Crypto-agility and extensibility, ensuring the platform can adapt to evolving standards and future cryptographic requirements
Accutive Security leverages its Innovation Lab, which hosts leading CLM platforms in fully functional environments, to design reference architectures and execute real-world proof-of-concepts. Rather than validating theoretical capabilities, these POCs test actual workflows, integrations, and failure scenarios under realistic conditions.
This approach enables organizations to identify strengths, limitations, and trade-offs early—before commercial commitments are made—reducing implementation risk and ensuring the selected platform aligns with long-term operational and security requirements.
5. What is your budget and how do you plan to staff your CLM/PKI program?
A sustainable PKI and CLM program requires more than the right technology—it requires a deliberate operating model that balances cost, expertise, resilience, and risk.
Organizations must evaluate how PKI and CLM responsibilities will be staffed and operated over time, taking into account:
- The scarcity and cost of experienced PKI talent, particularly as certificate lifecycles shorten and automation requirements increase
- Operational continuity and resilience, including coverage for vacations, attrition, and incident response
- The risk of single-resource dependency, which remains a common failure point in PKI programs
- The ongoing effort required to maintain and evolve CLM platforms, including integrations, policy updates, and roadmap execution
- Budget predictability, particularly as certificate volumes grow and automation increases issuance frequency
Many organizations determine that fully staffing PKI and CLM internally is impractical or cost-prohibitive. Managed and co-managed service models can provide access to specialized expertise, operational continuity, and scalable capacity without the burden of continuous hiring and training.
An experienced partner can also support commercial strategy and vendor negotiations, helping organizations avoid over-licensing, align contracts with actual usage patterns, and ensure pricing models support future growth and automation maturity.
By treating staffing and budget decisions as core components of PKI and CLM strategy—not afterthoughts—organizations can build programs that remain effective, resilient, and cost-efficient as certificate lifecycles continue to compress.
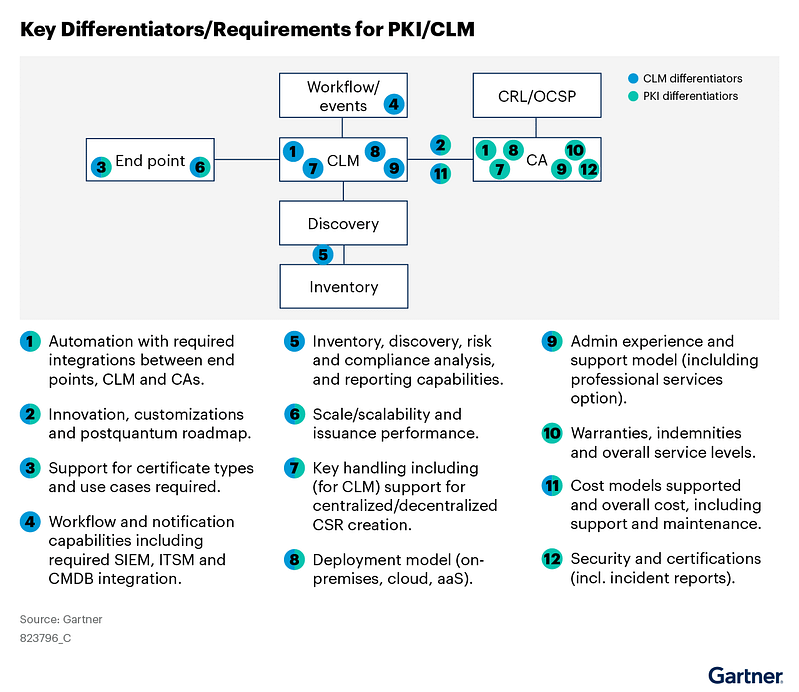
Compiling Your CLM/PKI Requirements
One of the most common reasons PKI and CLM initiatives fail to deliver long-term value is that requirements are either incomplete, improperly scoped, or overly tool-centric. As certificate lifecycles shorten and machine identity expands, requirements must be defined holistically across endpoints, automation layers, CLM platforms, and Certificate Authorities.
There are a number of different models that are used to elicit requirements for PKI/CLM programs. Gartner’s model (highlighted below) outlines that effective PKI programs depend on clearly defining requirements across three tightly coupled layers: endpoints, CLM, and PKI/CA services.
These layers cannot be evaluated in isolation. Decisions made at one layer directly influence scalability, automation, and risk at the others. For example, endpoint diversity and certificate consumption patterns drive automation and integration requirements within the CLM layer, while CA capabilities and constraints shape cryptographic controls, revocation models, and compliance posture.
By structuring requirements across these three layers, organizations can move beyond feature-driven tool selection and instead design PKI and CLM programs that align with operational realities, security objectives, and long-term roadmap goals. This approach reduces architectural gaps, avoids hidden dependencies, and ensures that PKI and CLM platforms can scale as certificate lifecycles continue to compress and machine identities proliferate.
Final Thoughts: PKI as Strategic Infrastructure
The shift toward 47-day certificates is a wake-up call that today’s security, compliance, and operational landscape can no longer be sustained with manual certificate management.
As certificate lifecycles continue to compress and machine identities proliferate across cloud platforms, DevOps pipelines, IoT, and operational environments, approaches that treat PKI and CLM as narrowly scoped, tactical solutions will increasingly fail to scale. Organizations focused solely on mitigating TLS renewal risk often discover that their tools, processes, and staffing models are insufficient to support the velocity, automation, and resilience now required.
By contrast, organizations that approach PKI as strategic infrastructure, anchored in clear business and risk objectives, well-defined use cases, a continuously evolving roadmap, disciplined platform selection, and a sustainable operating model, are far better positioned to absorb industry-driven change without disruption. These programs enable automation at scale, improve cryptographic agility, and materially reduce the operational and security risks associated with certificate-related failures.
2026 marks the point at which certificate management becomes inseparable from enterprise risk management, service availability, and regulatory compliance.
For security and technology leaders, the imperative is clear: the question is no longer whether PKI and CLM must evolve, but whether that evolution will be deliberate and strategic, or reactive and disruptive.










Comment