Over the last few years, the approach to cybersecurity has undergone a fundamental transformation. The old model of building a strong perimeter (a digital castle wall) and trusting everything inside is no longer suitable in a world of cloud services, remote work, sophisticated phishing attacks, and ever-present threats. The current model is Zero Trust, which is underpinned by the core mantra of “Never trust, always verify.”
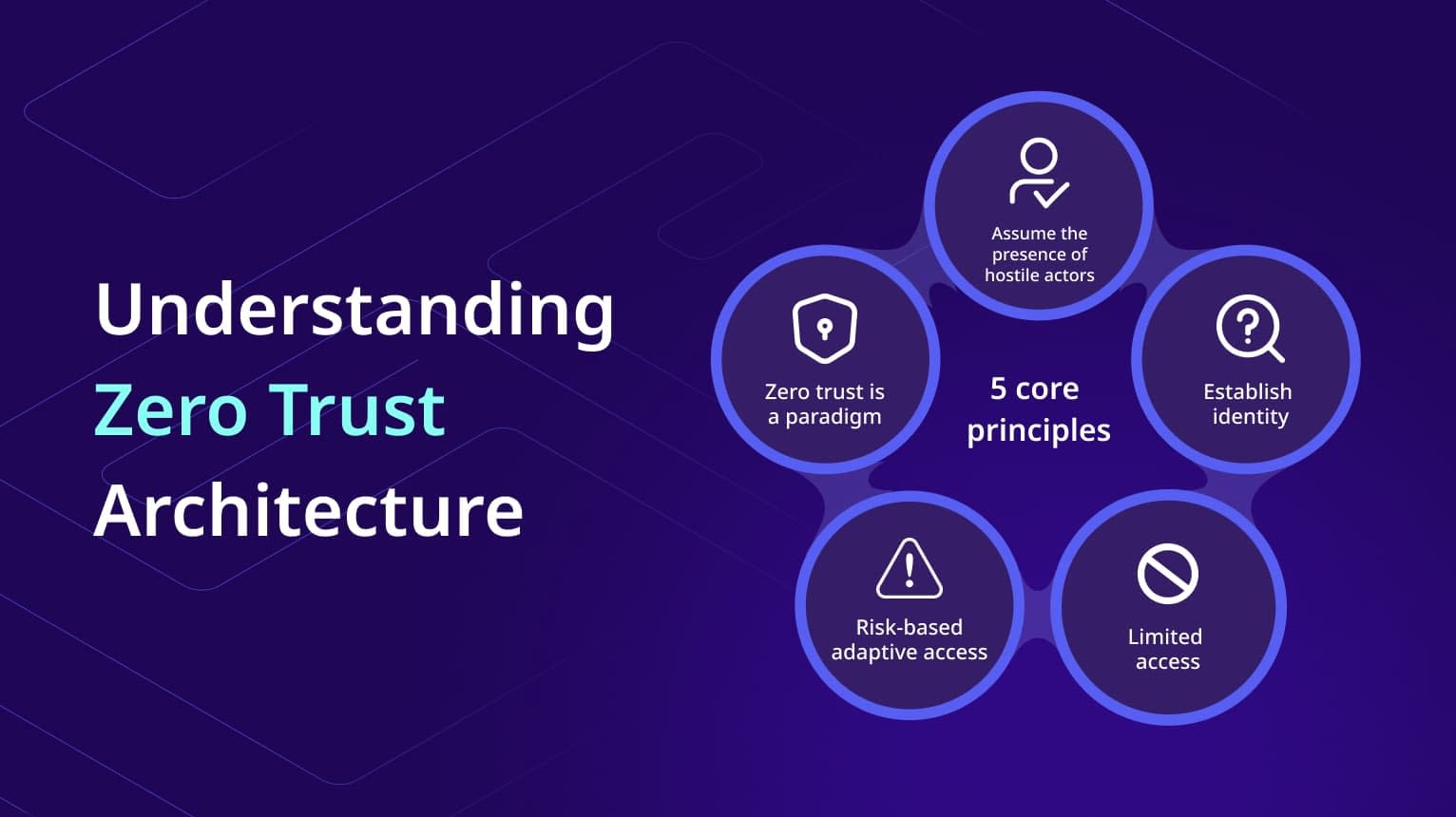
But what does Zero Trust mean in practice? Implementing Zero Trust involves building a comprehensive cybersecurity framework with several key components that is guided by core principles. It’s not a single product, but a strategic paradigm shift requiring integrated technologies spanning both human and machine identities.
Zero Trust Principle: Assume the Presence of Hostile Actors
Zero Trust strategy begins by fundamentally assuming hostile actors—external and internal—are already present within the environment. This ‘Assume Breach’ philosophy discards trust based solely on network location, acknowledging that modern perimeters are porous and attacks often bypass defenses or originate internally via compromised credentials. Security controls must therefore be effective even post-breach.
This perspective critically impacts Identity and Access Management (IAM). Credentials become prime targets, elevating scrutiny on every authentication and authorization. Strong, universally enforced Multi-Factor Authentication (MFA) becomes mandatory, as single factors are unreliable. With phishing attacks becoming more sophisticated, even traditional MFA is insufficient in many scenarios, necessitating physical security keys for an elevated level of protection. Identity behavior requires continuous scrutiny beyond initial authentication, and rigorous lifecycle management (especially prompt deprovisioning) is vital to remove latent attack vectors. The focus shifts decisively from trusting the network to verifying identity for every access request.
This also applies to cryptography, especially Public Key Infrastructure (PKI) and its associated components. Since network segments cannot be inherently trusted, PKI provides the critical cryptographic identities (digital certificates) needed to strongly authenticate devices, services, and potentially users, enabling secure, encrypted communication channels like mTLS even across potentially compromised networks. The integrity of this trust system, however, hinges on protecting its core elements. Safeguarding the highly sensitive private keys of Certificate Authorities (CAs) necessitates robust measures, often leveraging Hardware Security Modules (HSMs) for secure cryptographic key generation, storage, and operations. Furthermore, assuming breach implies that issued certificates could be compromised or misused; therefore, rigorous Certificate Lifecycle Management (CLM) becomes essential. CLM platforms automate the discovery, issuance, deployment, and particularly the rapid renewal or revocation of certificates, ensuring their validity is continuously verified and minimizing the window for exploitation by hostile actors.
Ultimately, assuming breach drives the need for continuous verification, strict least privilege access, adaptive controls, and comprehensive monitoring, all underpinned by strong identity management and pervasive cryptographic protection.
Zero Trust Principle: Establish Identity
Since trust isn’t assumed, identity becomes the primary control plane. Zero Trust demands that you first establish identity for every entity before granting access. This verification must be explicit and comprehensive, leveraging multiple components to handle both human and non-human (machine) identities:
Identity and Access Management (IAM) Systems: The core foundation for managing human identities, including:
- Identity Providers (IdPs) & Directory Services: Central repositories and authorities for user identities (e.g., Azure AD/Entra ID, Okta, Active Directory).
- Multi-Factor Authentication (MFA): Essential for verifying user identity using multiple factors, ideally employing phishing-resistant methods like FIDO2 hardware keys or smartcards (solutions often provided by specialists like HID Global or Thales).
- Privileged Access Management (PAM): Specialized controls and oversight for high-risk administrative accounts.
Machine Identity Management: Crucial for authenticating devices, services, applications, and APIs:
- Public Key Infrastructure (PKI): Issues digital certificates which serve as strong cryptographic identities for devices and services, enabling secure, authenticated communication protocols like mTLS. Requires careful management aligned with zero trust principles.
- Certificate Lifecycle Management (CLM): Platforms that automate the discovery, issuance, renewal, validation, and revocation of PKI certificates at scale – essential for managing potentially millions of machine identities and accommodating shorter certificate lifespans.
- Hardware Security Modules (HSMs): Secure cryptographic hardware often used to protect the private keys of critical PKI components like Root and Issuing CAs.
- Secrets Management: Systems designed to securely store, manage access to, and rotate secrets like API keys, service account passwords, and tokens used by applications and automation scripts.
Establishing strong, verifiable identities for all requesting entities through these integrated IAM and cryptographic mechanisms is the critical first step before determining appropriate access levels within a Zero Trust architecture.
Zero Trust Principle: Enforce Least Privilege
Once identity is strongly established and verified, Zero Trust dictates granting only limited access. This embodies the crucial Principle of Least Privilege (PoLP): provide the absolute minimum level of permissions necessary for that specific identity (human or machine) to perform its required function, for only as long as needed.
Enforcing PoLP is vital because, under the ‘Assume Breach’ model, compromised identities are an expected reality. Limiting the permissions associated with any single identity significantly contains the potential damage an attacker can inflict if they gain control of it. Over-privileged accounts are prime targets for privilege escalation and lateral movement. This principle is implemented through:
- Granular Access Policies: Defined within IAM systems and Zero Trust policy engines, often using Role-Based Access Control (RBAC) or more dynamic Attribute-Based Access Control (ABAC). Best in class solutions often include sophisticated policy management.
- Just-in-Time (JIT) Access: Granting privileges only temporarily when needed, rather than having them persist constantly.
- PAM Enforcement: As mentioned, PAM solutions are key to enforcing least privilege for administrative and other high-risk accounts through session control and credential vaulting.
- Cryptographically Bound Access: Permissions might be tied to possessing specific cryptographic credentials, like short-lived, role-specific certificates issued via PKI/CLM systems.
Zero Trust Principle: Adaptive Authentication
Essential for effective Zero Trust, Adaptive Authentication enables continuous, risk-based verification, rejecting static trust assumptions. It dynamically adjusts access controls and trust levels for both human and machine identities based on real-time context and risk signals evaluated throughout a session.
For human users, increased risk detected by IAM systems triggers adaptive responses. This often involves step-up MFA, demanding stronger proof like phishing-resistant FIDO smartcards and keys, or biometric factors managed. High-risk privileged operations can adaptively necessitate stricter controls enforced through Privileged Access Management (PAM) platforms, such as CyberArk PAM.
For machine identities managed via PKI, adaptive controls critically rely on Certificate Lifecycle Management (CLM) platforms for continuous certificate validation. An expired or revoked certificate acts as a definitive risk signal, immediately altering the trust posture and triggering access denial. Anomalous service behavior can also prompt adaptive cryptographic verification steps.
Adaptive Authentication intelligently operationalizes the “always verify” mantra. Orchestrated by adaptive engines, often integrated within broader IAM platforms, it translates risk signals into specific enforcement actions leveraging the organization’s integrated MFA, PAM, and CLM/PKI infrastructure, ensuring trust is continuously earned.
Zero Trust Architecture: Securing Human and Machine Identities Alike
A practical Zero Trust Architecture operationalizes the ‘never trust, always verify’ mandate, born from the foundational principle to Assume Breach. It functions as an integrated system where Identity and Access Management (IAM) and Cryptography provide the essential control plane and foundational trust anchors, moving security away from unreliable network location. Central to orchestrating Zero Trust decisions within this framework is the Policy Engine (Policy Decision Point – PDP).
Establish Identity
To Establish Identity for every access request the Policy Engine continuously consumes critical inputs from integrated security solutions. For human users, it relies on verified identity context provided by IAM platforms, validated by strong Multi-Factor Authentication (MFA) evidence. Effective zero trust architecture prioritizes phishing-resistant MFA factors, often leveraging FIDO smartcards ans security keys, or biometric/behavioral factors. For machine identities (devices, services, APIs), the engine validates strong cryptographic identities provided by Public Key Infrastructure (PKI) certificates. The trustworthiness, status, and lifecycle of these crucial certificates are actively managed by Certificate Lifecycle Management (CLM) platforms, providing vital attestation data to the Policy Engine.
Enforce Least Privilege
Based on this rigorously verified identity, the Policy Engine then applies authorization policies meticulously designed to Enforce Least Privilege. These policies ensure that the authenticated entity receives only the minimum necessary permissions required for its specific task, limiting the potential impact should that identity be compromised (reinforcing the Assume Breach strategy). This enforcement often integrate checks with Privileged Access Management (PAM) systems for governing and auditing high-risk or administrative access requests.
Adaptive Authentication
Crucially, Adaptive Authentication enables continuous verification. The Policy Engine incorporates real-time risk signals – derived from behavioral analytics, threat intelligence feeds, contextual data like location or time, and critical certificate status updates reported by CLM systems. This allows policy rules and enforcement actions, such as requiring step-up MFA or altering permissions mid-session, to dynamically adapt based on the currently assessed risk level associated with the identity and its requested action.
Putting It All Together: Zero Trust Architecture
The integrity and security of this entire decision-making process, especially vital under the Assume Breach model, rests heavily on robust cryptographic foundations woven throughout the architecture. PKI not only provides verifiable identities but also enables secure, mutually authenticated communication channels like mTLS, essential even across internal network segments. The security of the PKI itself is often bolstered by Hardware Security Modules (HSMs), which protect critical private keys. Complementing PKI, Secrets Management platforms securely handle the lifecycle of non-PKI credentials used by applications and services.
Finally, the Policy Engine translates its context-aware decisions into instructions for distributed Policy Enforcement Points (PEPs)—such as gateways, proxies, agents, or service mesh sidecars—which implement the calculated access control (allow, deny, limit, step-up). This ensures access is granted based on continuous, policy-driven, context-aware validation, truly embodying the Zero Trust paradigm.
Building Your Zero Trust Architecture
Zero Trust represents a necessary evolution in cybersecurity strategy, moving decisively away from outdated perimeter-based models. It’s a paradigm built on core principles: Assume Breach, demanding vigilance against both external and internal threats; Establish Identity, requiring rigorous verification for every user and machine; Enforce Least Privilege, strictly limiting access to only what is necessary; and leverage Adaptive Authentication, continuously adjusting trust based on real-time risk.
Operationalizing these principles through a Zero Trust Architecture requires a deep commitment to integrating robust Identity and Access Management systems with foundational cryptographic technologies – including advanced MFA, Privileged Access Management, comprehensive PKI and Certificate Lifecycle Management, Hardware Security Modules, and secure Secrets Management.
While the journey to a mature Zero Trust posture requires ongoing effort, assessment, and adaptation, the benefits are clear. By centering security around identity and leveraging modern IAM and cryptographic controls, organizations can build a more dynamic, resilient defense better equipped to protect critical assets against the sophisticated and pervasive threats of today’s digital landscape. It is an essential strategic imperative for meaningful risk reduction and future readiness.










Comment