Managing digital certificates might sound simple, but for most organizations, it’s anything but not simple. For cryptography and IT teams handling hundreds of certificates, staying ahead of expirations, maintaining security, and meeting compliance demands are constant challenges. Here’s an in-depth look at why having robust certificate lifecycle management processes is essential, the obstacles organizations face, and how certificate lifecycle management practices help teams stay resilient.
According to Keyfactor, 77% of organizations have experienced outages due to unexpected certificate expirations, costing companies up to $72,000 per hour in downtime. This article breaks down the main issues teams face daily, from lost certificates and renewal overloads to navigating compliance audits.
What is Certificate Lifecycle Management?
Certificate Lifecycle Management refers to the processes involved in managing and overseeing each stage of a certificate’s lifecycle, from discovery and issuance to renewal and decommissioning.
For example, nearly every enterprise’s infrastructure includes external TLS/SSL certificates for secure web traffic, client certificates for secure system access, and device certificates for IoT endpoints. Managing these manually can lead to visibility gaps, security lapses, and costly outages. Centralized certificate lifecycle management ensures certificates are consistently managed, tracked, and monitored, significantly reducing risks.
However, proper certificate management goes beyond simply keeping your certificates up-to-date. A robust certificate management strategy consolidates oversight across environments, reduces human error, strengthens security, and supports compliance.
Types of Certificates and Their Unique Challenges
Different types of certificates serve unique functions, each with specific management requirements that add complexity to your certificate management solution.
- TLS/SSL Certificates: These are essential for secure web traffic and are among the most frequently renewed due to short lifespans. A lapse in TLS/SSL management risks customer trust and web application security.
- Code-Signing Certificates: Used to authenticate software integrity, these certificates are critical in development environments where unauthorized code could lead to vulnerabilities. Certificate management tools ensure these certificates are tracked and updated without disrupting the development process.
- Email Certificates (S/MIME): These secure email communications with encryption and signatures, critical for user privacy. Without certificate management tools, tracking each certificate’s lifecycle is challenging, especially when protecting sensitive email data.
- Device and Client Certificates: These certificates authenticate access for devices and users, commonly in IoT and internal applications. Certificate management tools monitor and update these certificates across distributed systems to prevent unauthorized access from rogue devices.
By centralizing certificate management, certificate management solutions help IT teams address each certificate’s specific requirements without missing renewals or risking security.
Why Today’s IT Landscape Demands Certificate Lifecycle Management
For cryptography and IT administrators, managing certificates goes beyond tracking a single certificate from issuance to revocation. Each type—be it TLS/SSL, code-signing, or device certificates—has unique management needs, which multiply as these certificates increase in volume and complexity. This life cycle includes discovery, issuance, monitoring, renewal, and decommissioning, all of which need consistent oversight across thousands of certificates in different systems.
With the average enterprise managing more than 25,000 certificates annually, it’s clear that tracking, renewing, and maintaining each certificate manually is impractical. The risk of “certificate sprawl” is high, with certificates scattered across cloud platforms, on-prem environments, and third-party applications.
The imminent shortening of TLS certificate validity periods from 398 to 90 or even 45 days compounds these challenges. The amount of work associated with each manually managed certificate is expected to increase 5 or even 10 fold. The expected need to switch to quantum ready certificates will compound this challenge even further. If you lack a robust CLM, you may be facing a massive, complex discovery, revocation, and reissuance process that could overwhelm your team, disrupt your operations, increase the risk of outages, and shake your customer’s confidence.
A robust certificate lifecycle management process centralizes certificate oversight, bringing every certificate under unified management, ensuring that no certificate is overlooked, and reducing costly disruptions.
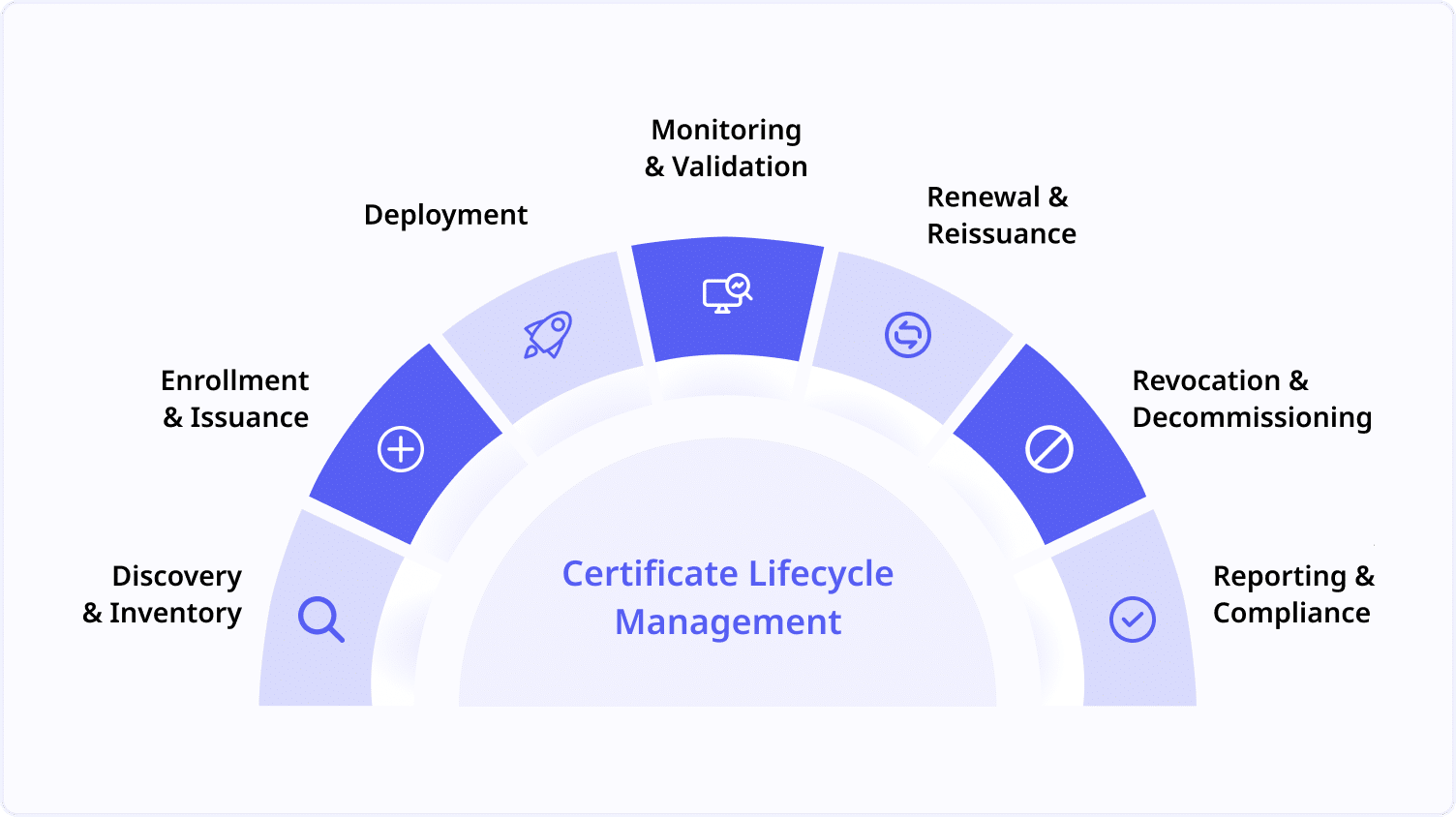
Managing Every Stage of the Certificate Lifecycle
Each stage in the certificate lifecycle requires careful attention to maintain visibility, strengthen security, and prevent costly downtime. Here’s how certificate lifecycle management keeps each phase on track:
- Certificate Discovery and Inventory: Finding every certificate across all environments is the first step. Automated discovery tools scan networks, bringing each certificate into a single inventory that provides a clear view of all certificate deployments. Research indicates that without active discovery, around 40% of expired certificates remain undetected, which can expose organizations to serious security risks. Certificate lifecycle management eliminates “ghost” certificates, giving IT teams a complete, organized inventory.
- Certificate Enrollment and Issuance: Requesting and obtaining new certificates starts with generating a Certificate Signing Request (CSR) and submitting it to a Certificate Authority (CA). Once issued, each certificate must be assigned to its designated owner and readied for deployment. This process can easily go awry if certificates are misassigned or left unmonitored. Certificate lifecycle management tracks each issuance, assigning ownership and making sure certificates land where they’re needed, without the guesswork.
- Certificate Deployment: Once issued, certificates must be configured and deployed to their intended servers, devices, or applications. Each system needs to recognize and use the certificate properly, whether it’s securing web traffic, authenticating users, or encrypting communication. Certificate lifecycle management supports seamless deployment across environments, so IT teams can be confident that certificates are installed correctly, preventing exposure from misconfigurations.
- Certificate Monitoring and Validation: Continuous monitoring ensures certificates stay active, healthy, and compliant. By tracking certificates in real time, certificate lifecycle management allows IT teams to identify and fix potential issues before they escalate into outages or security breaches. Automated alerts notify teams of expiring or compromised certificates, making it easy to stay ahead of disruptions and protect critical services.
- Certificate Renewal and Reissuance: All certificates have expiration dates, requiring regular renewal to avoid lapses in service. The renewal process often mirrors issuance, requiring a new CSR and approval from a CA. Managing renewals manually increases the chance of missed expirations. Certificate lifecycle management automates renewals, reissuing certificates seamlessly and minimizing human error so IT teams can focus on more critical tasks without fearing unplanned service interruptions.
- Certificate Revocation and Decommissioning: Sometimes certificates need to be revoked—perhaps due to security compromises or redundant credentials. Revoking removes a certificate from active use, while decommissioning retires it completely from the system. Without proper revocation, old certificates could create security risks. Certificate lifecycle management enforces revocation policies, making sure expired or unnecessary certificates are securely decommissioned, reducing unauthorized access risks.
- Certificate Reporting and Compliance: Reporting on certificate status and compliance is essential to both cybersecurity and operational success. With regular reporting, certificate lifecycle management offers insights into certificate health, usage, and compliance with internal policies or external regulations. Consistent logging and compliance reporting keep organizations audit-ready, simplifying the review process and helping IT teams stay aligned with evolving standards.
Operational Challenges in Certificate Lifecycle Management
1. Visibility Gaps and Ghost Certificates
When different departments manage certificates independently, some become “ghost certificates”—untracked and forgotten until they expire, creating security vulnerabilities. Certificate lifecycle management discovers and inventories all certificates, maintaining visibility and reducing risks of unplanned expirations.
2. Renewal Overload and Manual Processes
With shorter certificate lifespans, frequent renewals can become unmanageable when handled manually. Certificate lifecycle management automates renewals, issues proactive alerts, and keeps certificates up-to-date, freeing IT staff to focus on critical tasks rather than chasing renewals.
3. Fragmented Management Across Teams
In complex setups, different departments managing their own certificates lead to wasted resources and missed renewals. This siloed approach hinders consistent visibility. Certificate lifecycle management centralizes data into one dashboard, improving collaboration and ensuring up-to-date certificate status across the organization.
4. Compliance and Audit Complexity
Meeting regulatory standards requires precise documentation of certificate activities, which is challenging with disjointed tracking systems. Certificate lifecycle management automates audit-ready logs, providing a clear history of each certificate’s lifecycle, from issuance to revocation. This streamlines compliance and simplifies audit preparation.
5. Service Outages from Expired Certificates
Unexpected expirations disrupt critical applications, damaging customer trust. Certificate lifecycle management provides real-time monitoring and automated renewals, helping IT teams stay ahead of expiration dates and avoid outages impacting operations and reputation.
6. Preparing for Crypto-Agility
With advancing cryptographic standards, IT teams must regularly update certificates to maintain security, especially as quantum computing becomes more feasible. Manually updating certificates is time-intensive and prone to errors. Certificate lifecycle management with crypto-agility capabilities enables smooth transitions to new encryption standards, future-proofing security.
Choosing the Right Certificate Management Solution
For IT teams grappling with certificate sprawl, unexpected expirations, and complex hybrid environments, solutions from Venafi and Keyfactor provide robust features, such as automated certificate discovery, renewal workflows, and centralized management dashboards.
- Venafi TLS Protect
Venafi TLS Protect offers a unified, cloud-based approach to certificate management, providing centralized visibility into all TLS machine identities. By automating discovery and renewal processes, Venafi ensures certificates are renewed well in advance, eliminating the risk of outages from expired certificates and reducing the strain on IT teams. For organizations prioritizing continuity and comprehensive TLS security across environments, Venafi TLS Protect addresses these critical challenges directly. - Keyfactor Command
Keyfactor Command is built to simplify these tasks, offering automation across PKI and machine identity management. With flexible deployment options—whether on-prem, SaaS, or fully hosted—Keyfactor Command adapts to unique infrastructure needs, enabling IT teams to issue, monitor, and renew certificates without the risk of manual errors. For IT departments focused on reducing manual intervention and maintaining full PKI oversight, Keyfactor Command provides a reliable, adaptable solution.
When evaluating certificate management solutions, consider factors like the level of automation, compatibility with multi-cloud environments, and integration with broader security systems.
5 Considerations When Implementing Certificate Lifecycle Management
Implementing certificate lifecycle management can transform how your organization handles security and compliance, but certain hidden challenges can impact its success. By identifying these key considerations early on, IT teams can ensure a smoother, more effective rollout and ongoing management of certificate lifecycle management.
- Scaling with Growing Certificate Volume
As digital assets expand, so does the certificate load, and not all certificate lifecycle management solutions can handle high volumes seamlessly. Without the right system, scaling up can lead to performance issues or bottlenecks. Look for certificate lifecycle management designed to manage substantial certificate volumes, ensuring smooth operations as your digital footprint grows - Integration with Legacy Systems
Many organizations rely on legacy systems that don’t always integrate smoothly with newer tools. Certificate lifecycle management solutions with strong API support or integration capabilities can bridge these gaps, allowing IT teams to manage certificates effectively across both legacy and modern environments, ensuring nothing slips through the cracks. - Managing Mixed Environments
Hybrid, multi-cloud, and on-premises setups introduce complexity to certificate oversight, often resulting in siloed certificates. This fragmented approach can lead to visibility gaps, making it harder to monitor certificate health across the board. Choose a certificate lifecycle management solution that offers centralized visibility across all environments, making it easier to track and manage certificates wherever they reside. - Human Error and Setup Complexity
Even with automation, certificate lifecycle management systems can be complex to set up and maintain. Misconfigurations during setup or routine maintenance can lead to security vulnerabilities or operational issues. A certificate lifecycle management solution with a user-friendly interface, role-based access control (RBAC), and detailed onboarding resources helps reduce these risks, enabling IT teams to operate securely and efficiently. - Addressing Shadow IT and Unaccounted Certificates
Shadow IT—certificates issued outside the IT team’s oversight—can introduce significant security risks. With periodic discovery scans, a robust certificate lifecycle management solution brings rogue certificates under management, reducing unauthorized access points and helping IT teams gain full control over the certificate landscape. - Leveraging Analytics for Better Management
Integrating analytics into your certificate lifecycle management system provides actionable insights that go beyond simple tracking. Analytics on certificate usage, expiration, and renewal patterns help IT teams anticipate needs, allocate resources efficiently, and prevent overloads from a surge of renewals.
Taking these considerations into account ensures that your certificate lifecycle management system is set up for success, providing lasting security benefits and empowering your IT team to manage certificates efficiently across your entire infrastructure
Demonstrating ROI from Certificate Management Tools
Implementing a certificate lifecycle management solution requires an upfront investment, and proving its ROI can be challenging, especially when the savings are indirect. However, a well-integrated certificate lifecycle management system can deliver a 4-10x return by preventing costly security incidents and streamlining everyday operations.
Certificate lifecycle management is more than just another tool; it’s a strategic way to secure your organization’s infrastructure and keep things running smoothly. But to get the most from it, especially in complex setups, you need a solution that fits your organization’s specific needs, not a one-size-fits-all approach.
That’s where experts like Accutive Security make the difference. Rather than just implementing a certificate management tool, they tailor it to your organization’s specific infrastructure, compliance needs, and security goals. By aligning your certificate management tool with your regulatory requirements, hybrid systems, and day-to-day processes, Accutive Security ensures the system isn’t just running in the background—it’s seamlessly integrated into workflows in a way that actually makes work easier.
Conclusion: Turning Certificate Lifecycle Management into a Strategic Advantage
Managing digital certificates is no longer just an item on the IT to-do list; it’s a foundational element of securing digital infrastructure and ensuring operational continuity. The right certificate management approach enables IT teams to not only stay ahead of expirations and compliance demands but also anticipate and solve the hidden issues that often get overlooked.
With Certificate Lifecycle Management, IT gains centralized control over certificates across environments, supporting security frameworks like zero-trust, where every certificate is verified to minimize access risks. As cryptographic needs evolve, Certificate Management ensures readiness, enabling smooth transitions to new standards without compromising security.
Key Takeaways:
- Enhance Uptime: Proactive monitoring and real-time alerts reduce downtime, keeping services uninterrupted.
- Strengthen Security: Centralized control supports zero-trust principles and secure certificate interactions across systems.
- Future-Proof Operations: CLM adapts to new cryptographic standards, ensuring long-term data protection.
Certificate lifecycle management, when done right, becomes a strategic advantage. It gives IT teams the tools to unify certificates across legacy and modern environments, actively mitigate downtime risks, and seamlessly adapt to emerging cryptographic standards.
Ultimately, certificate management helps IT teams breathe easier. Instead of constantly reacting to certificate problems, they can focus on building a robust, future-ready infrastructure. For organizations that rely on secure, uninterrupted operations, certificate management isn’t just helpful; it’s transformative.












Comment