ADM's Data Discovery tools find PII and other sensitive data across all your databases
Automated Data Discovery platform configurable to your data compliance needs, including PII, PCI, HIPAA, PIPEDA, CCPA, GDPR + more. Discover and mask your data in mere minutes.
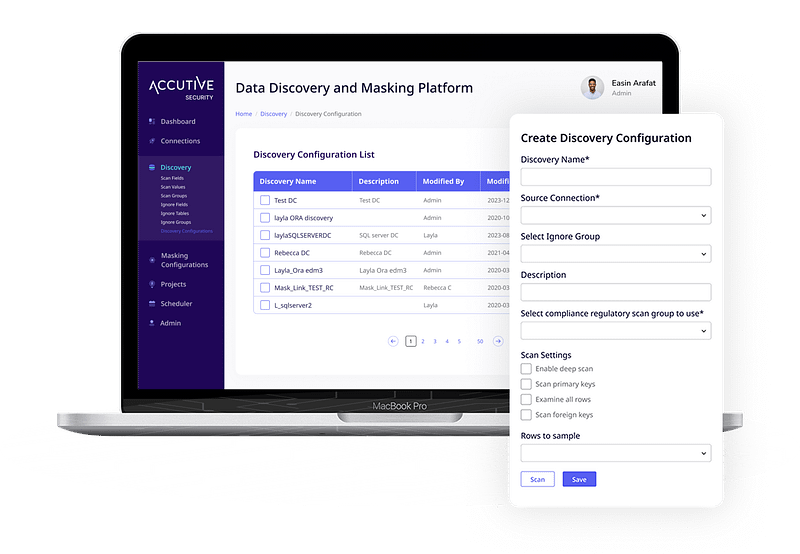
Transform Your Test Data Management

Data Discovery
Key Benefits of ADM, the platform that finds sensitive data everywhere
Rapid + accurate data discovery
Affordable data discovery software
Automated sensitive data discovery based on your compliance needs
Fully customizable data discovery that is scalable to your needs + industry
Data discovery for all major file types and databases, including Microsoft SQL Server, Oracle Database, MySQL, PostgreSQL + more
Key Benefits for your Organization
Avoid costly data breaches or exposures by finding unknown sensitive data
Effective platform for auditing, analytics, and M&A
Enhance data quality by boosting your data hygiene
Contextualize, analyze, and optimize your data
Empowering you to stay in compliance
$4.45M in cost avoidance
per data breach based on the average cost of a data breach in 2023, according to IBM Security

#1
Data Masking Solution
Data Masking Software
ADM has been successfully deployed as the preferred test data management solution for our North American clients across various industries including:
- Financial Services
- Healthcare
- Post-secondary education
- Public sector
- Software Development
- Project Management Consulting
- Legal
Accelerate your data discovery and data masking

Understand Your Needs
Understand Your Needs

Discover Sensitive Data
Discover Sensitive Data

Configure Masking Easily
Configure Masking Easily
Mask + Deploy in Minutes
Mask + Deploy in Minutes

ADM makes regulatory compliance easy with sensitive data discovery across all major databases including:

Looking for expert support for your data discovery needs?
Explore our Data Discovery Services
An Advanced Data Security Platform
Data Masking
Enable test and QA teams with fully protected, masked production data securing sensitive information, ensuring compliance and accelerating results.


Data Discovery
Data Subsetting


Data Automation
Data Tokenization
Substitute your critical sensitive data with a non-sensitive placeholder for secure usage + sharing.
An Advanced Data Security Platform
Data Masking
Enable test and QA teams with fully protected, masked production data securing sensitive information, ensuring compliance and accelerating results