Articles
Explore Topics

Data Masking for the Banking Industry: Key Considerations for Financial Institutions
The financial industry is built on trust, and a crucial component of that trust is

Understanding Passkeys and Hardware Tokens: Building phishing-resistant authentication
Phishing attacks evolved far beyond the poorly written email scams they were known for. Cybercriminals

CISO Challenges for 2025: Overcoming Cybersecurity Complexities
As organizations recognize the immense value and criticality of your data and systems, cybersecurity has

How to Choose the Right Test Data Management Tools
In today’s fast-paced, compliance-focused world, choosing the right test data management (TDM) tools is vital

Post-Quantum Cryptography: The Implications of Google’s Willow and Other Quantum Computers for Cybersecurity
Quantum computing was long considered to be part of a distant future. However, it is

Apple 45-Day Certs: Implications for Certificate Lifecycle Management
Remember when we were bracing ourselves for 90-day certificates? Google’s proposed move to 90-day TLS

5 Powerful Integrations with Thales HSMs (Hardware Security Modules)
Organizations managing sensitive data know that securing encryption keys and ensuring regulatory compliance are non-negotiable.

Navigating Certificate Lifecycle Management
Managing digital certificates might sound simple, but for most organizations, it’s anything but not simple.
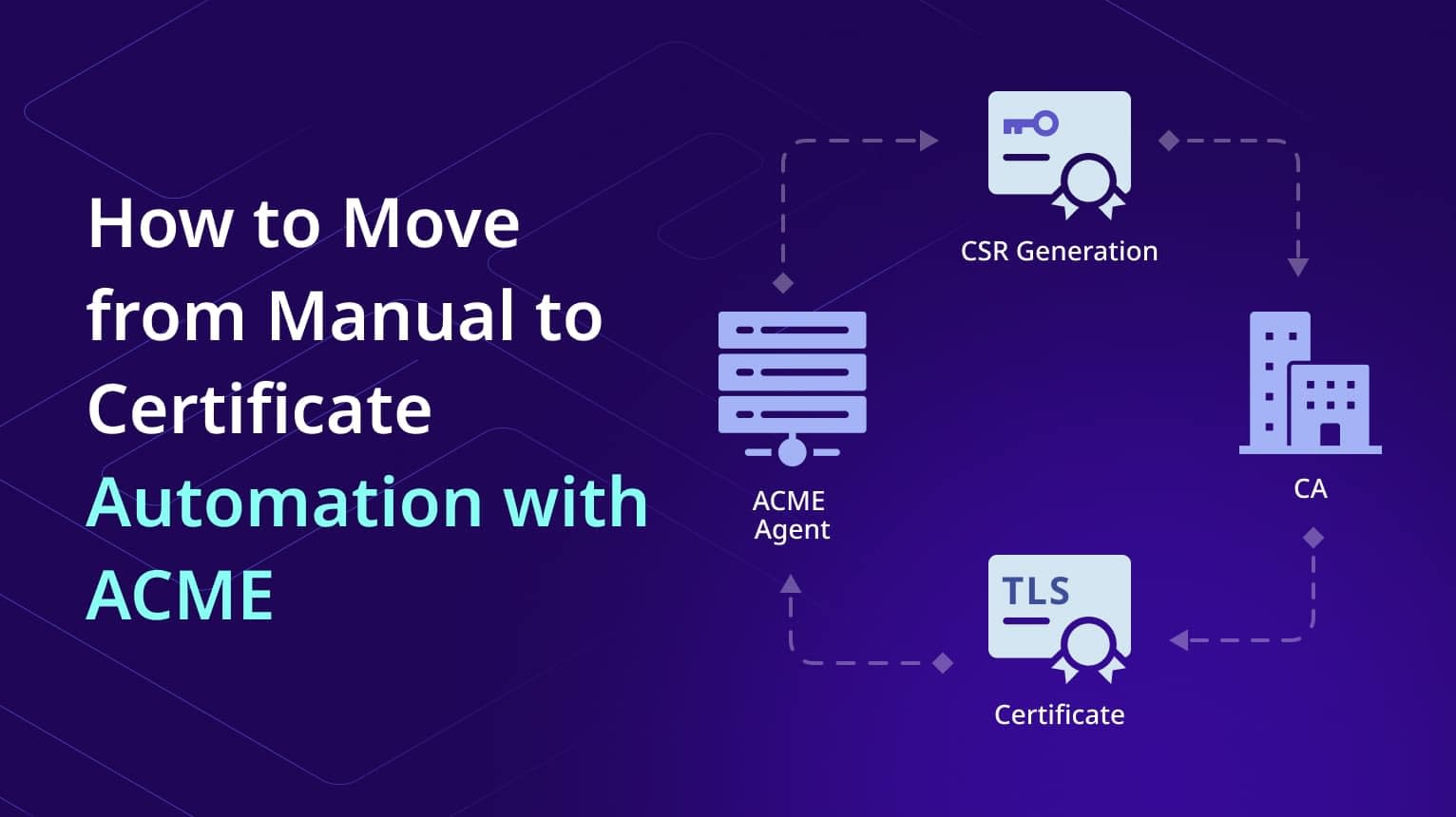
How to Move from Manual to Certificate Automation with ACME
For IT teams, managing certificates can feel like a relentless cycle of tracking expiration dates,

Sensitive Data Discovery for Enterprises: Turning Data Chaos into Compliance
In today’s data-driven landscape, sensitive information—like PII (Personally Identifiable Information), PHI (Protected Health Information), and


