
Healthcare Technology company used ADM to discover, protect + mask billions of rows of sensitive data


Reduce the risk of data breaches and protect sensitive information, ensuring a robust defense against cyber threats.

Meet legal requirements for data privacy and protection, avoiding fines and penalties associated with data mishandling.

Decrease the likelihood of costly data breaches and the associated expenses of damage control and legal fees.

Enable thorough and secure testing, leading to higher-quality software products and fewer post-release defects or issues.

Build customer and stakeholder trust by demonstrating a commitment to data privacy and security, enhancing brand reputation.

Accelerate development processes by allowing safe use of real-world data scenarios without compliance roadblocks or privacy concerns.
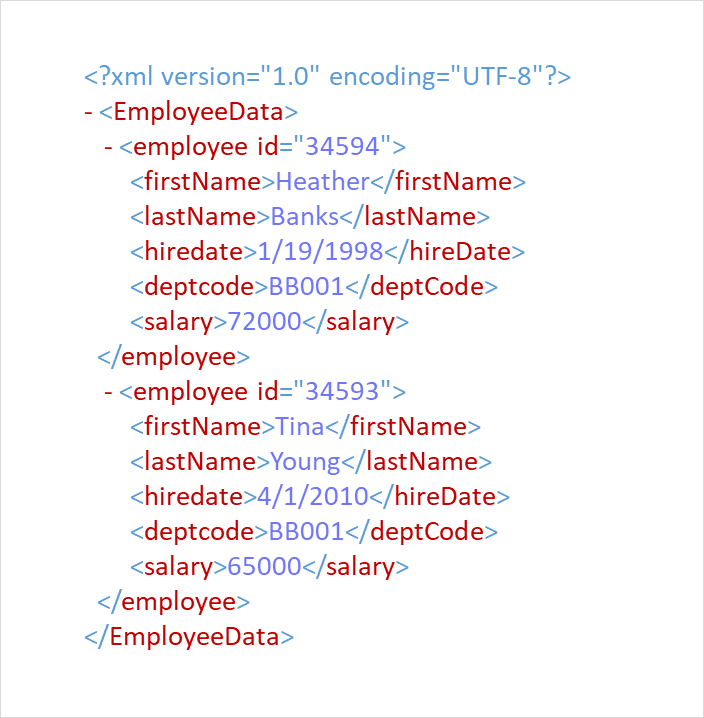
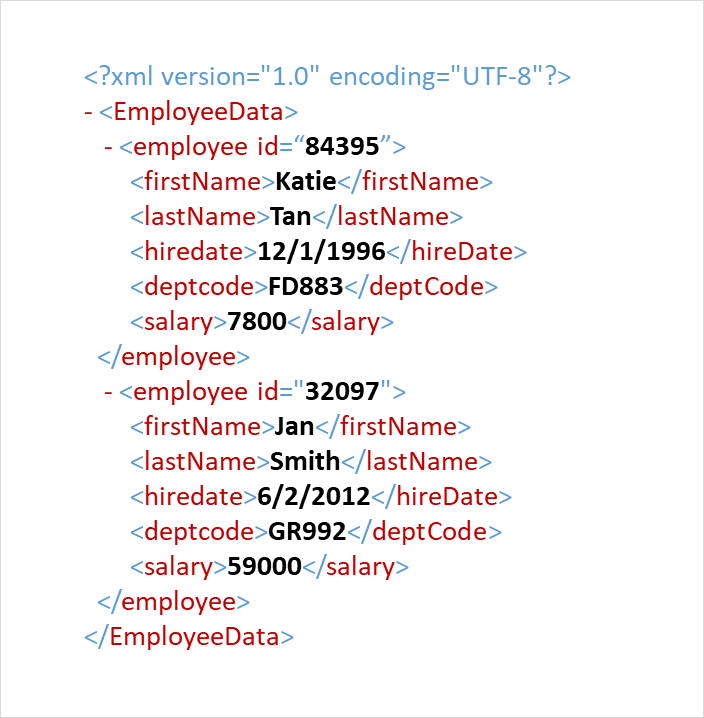
Seamless XML Content Masking
Ensure your personal data remains protected during development and testing—without breaking XML schema or important application logic.
Your Flat Delimited Files, Covered
Protect sensitive data stored in a range of files types to comply with data regulations and mandates
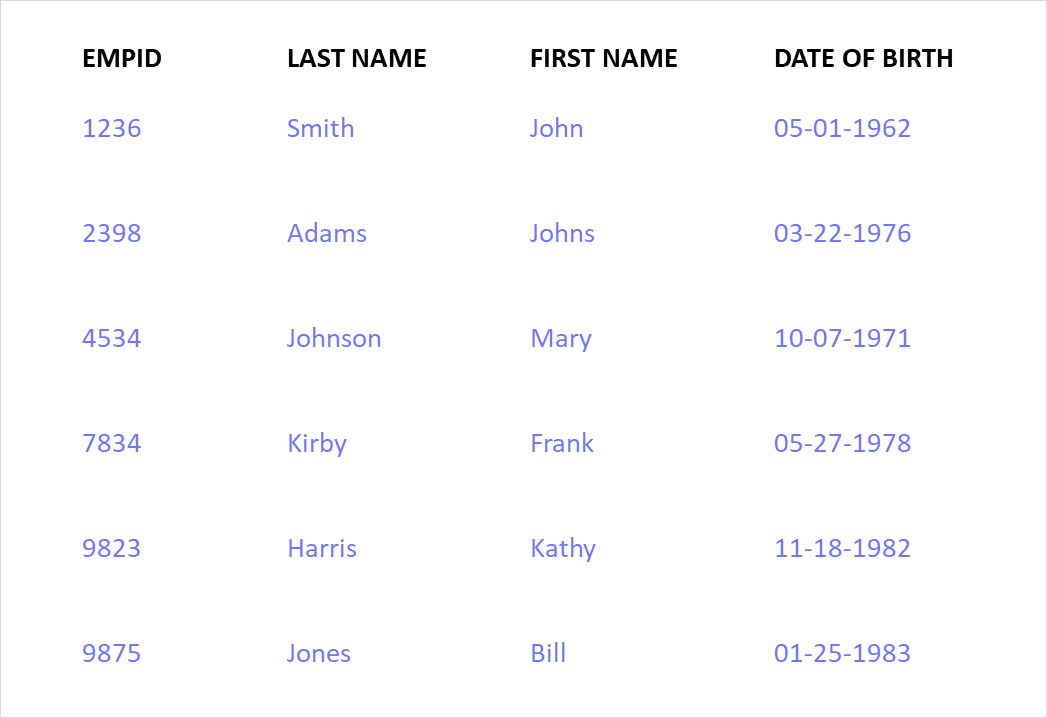
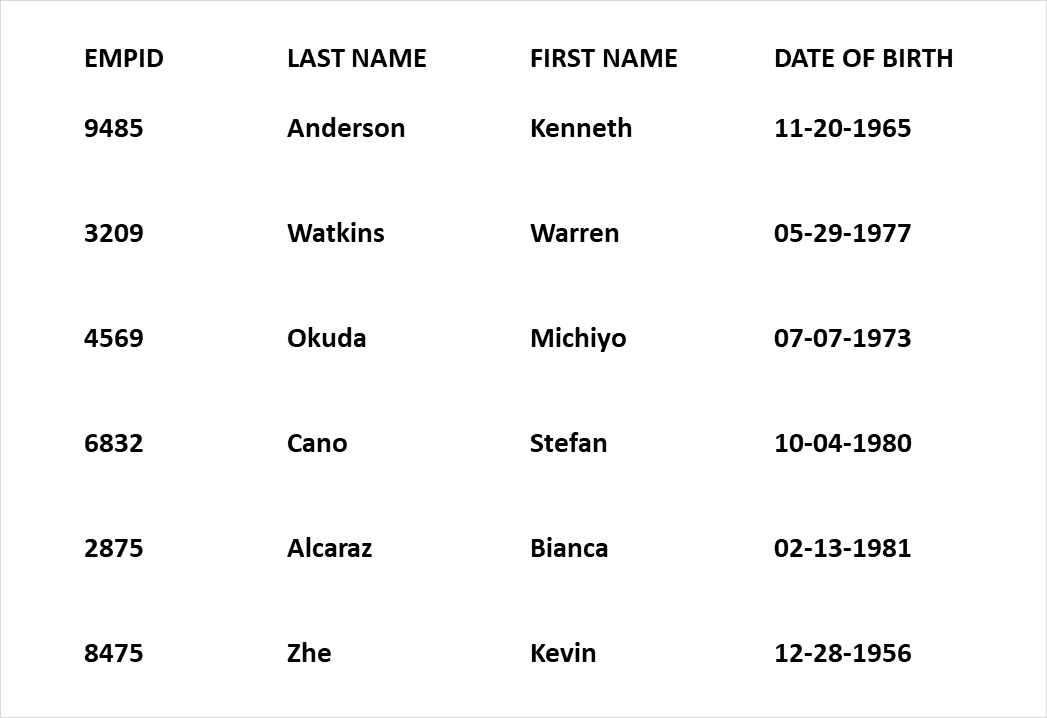
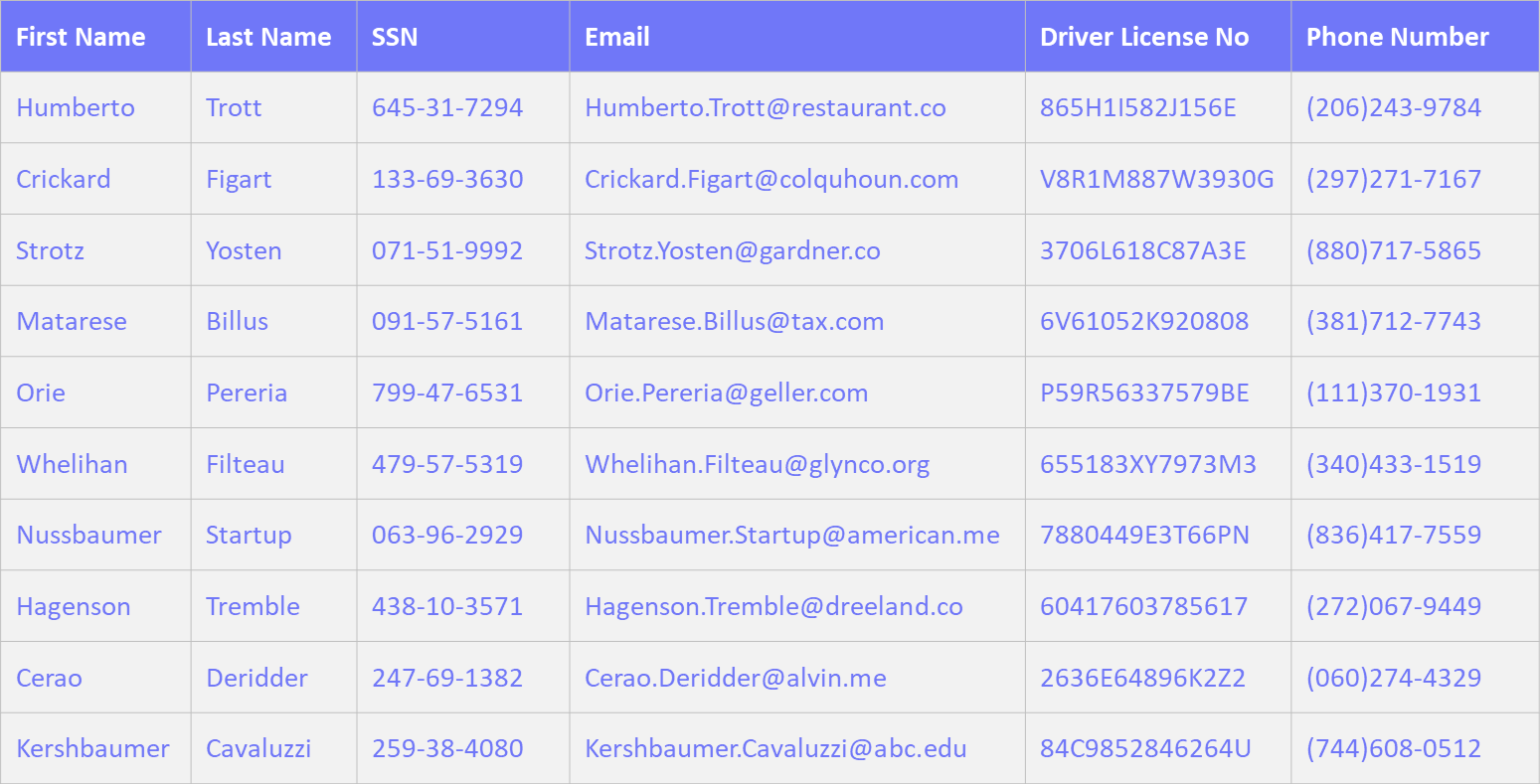
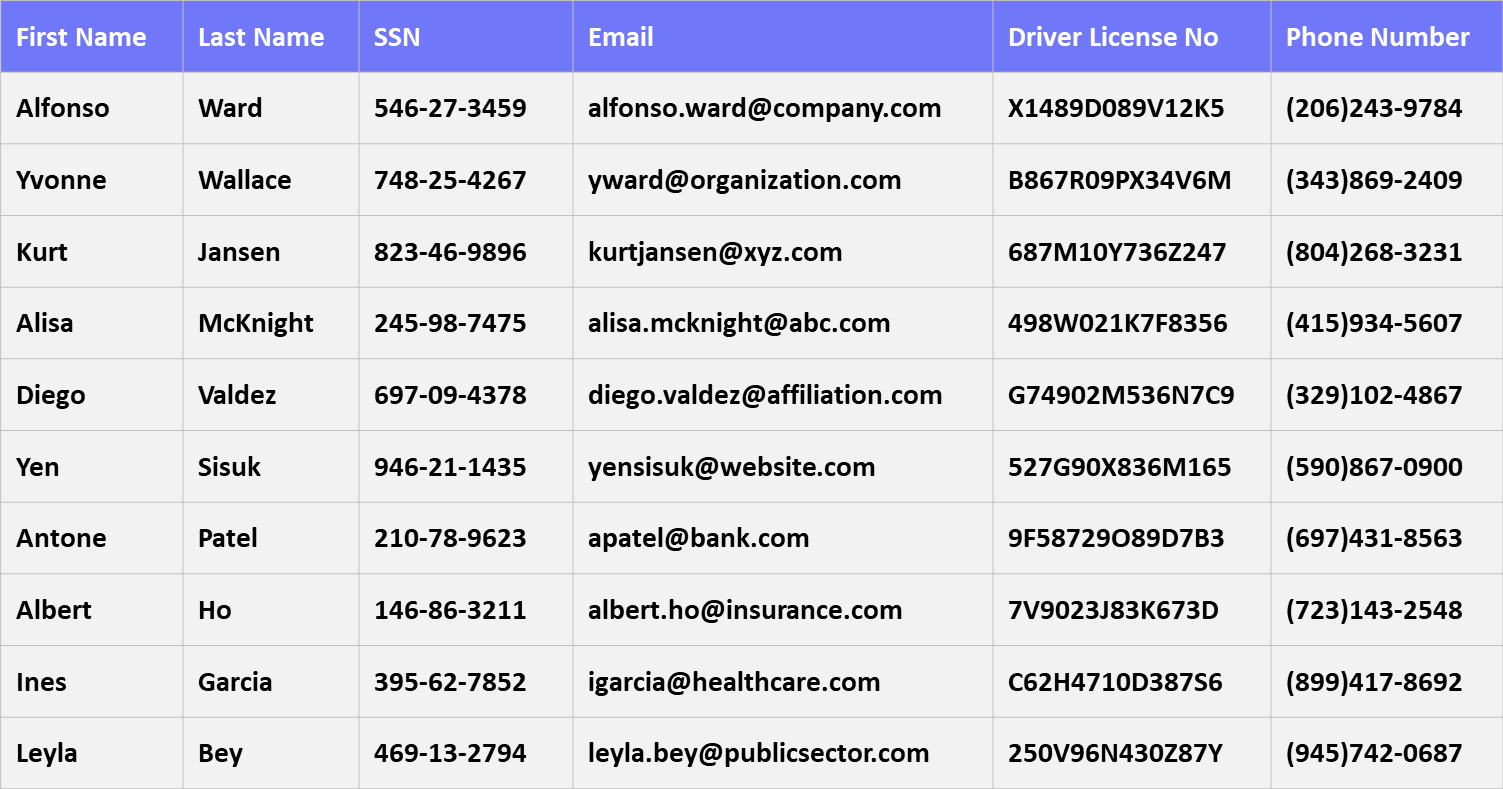
Robust Database Masking for Security and Compliance

Lack of rapid planning and execution
Increased complexity of DataOps and security needs for effective solutions

Potential fines, reputation damage and data loss
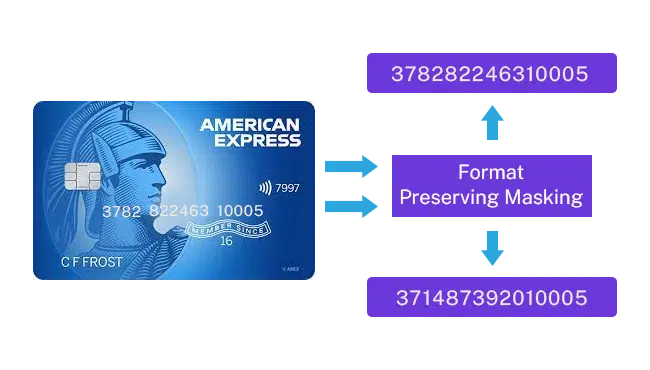
Example 1: Format-Preserving Masking retains data structures, like American Express card format, for system validation without revealing actual card details.
Example 2: Luhn Algorithm Masking creates valid-looking numbers that pass the Luhn check, ensuring realistic, non-active data representation in systems.
Example: An SSN such as 109-98-1767 (not real but adheres to the standard—109 shows it was issued in NY) can be masked as 109-00-5874 consistently across all other databases, files, and more.
With ADM, you can use our advanced pre-configured Groovy Scripts, or create your own to overcome any data masking challenge – no matter how complex.

ADM allows to you to mask information while maintaining important categories for your data
Example: Mask a user’s age with a fictional number that is still within the same age group as the original. A senior citizen will remain a senior citizen, and a teenager will remain a teenager.
Show More
Compound masking allows you to mask unique, interconnected fields.
Example: If a first and last name are masked into new values, an original email address derived from the name will automatically be generated with the new values.
Show More
ADM allows you to maintain related fields, so your data remains logical.
Example: When changing a user’s age, their birthday will also automatically adjust, maintaining continuity and logic.
Show More

Supports Data Discovery + Data Masking for all major Databases and Information Management Tools including Oracle Database, Microsoft SQL Server, MySQL, PostgreSQL, IBM DB2, Amazon RedShift, MongoDB and more.

