For IT teams, managing certificates can feel like a relentless cycle of tracking expiration dates, renewing certificates, and monitoring CA chains. Without automation, it’s easy to miss renewals, leading to costly outages and downtime. As your organization scales, manually managing hundreds—or even thousands—of certificates quickly becomes unsustainable. With the imminent shortening of certificate validity periods to 90 or 45 days, the need for certificate automation has never been greater.
Once you understand that you need to automate, the next question is how? The first step is selecting a certificate lifecycle management platform with automation capabilities. Accutive Security partners with leading certificate lifecycle management (CLM) vendors like Venafi and Keyfactor to implement advanced, automation-ready solutions.
After your CLM solution is implemented, the next step is to integration and automation. There are several different approaches to certificate automation. One common approach is to leverage the open-source protocol Automatic Certificate Management Environment (ACME).
ACME provides a standardized way for clients (like web servers or other applications) to automatically request and renew certificates from a certificate authority (CA). Its simplicity, affordability and wide adoption make it a popular choice for organizations seeking to streamline certificate management.
In this guide, we’ll dive into the benefits of transitioning from manual processes to ACME-driven automation and offer a practical roadmap to ensure a smooth shift.
The Role of ACME in Certificate Automation
Manual certificate management is fraught with challenges. IT teams often juggle spreadsheets, calendar reminders, and manual processes to track expiration dates, renew certificates, and maintain CA chains. This approach is not only time-consuming and error-prone but also exposes organizations to significant risks:
- Missed Renewals: Expired certificates can lead to service outages, downtime, and frustrated users, impacting productivity and revenue.
- Accidental Deletions: Critical systems can grind to a halt if a certificate is accidentally deleted, requiring urgent and often complex recovery efforts.
- Security Vulnerabilities: Manual processes increase the likelihood of human error, potentially leaving systems vulnerable to security breaches and compliance violations.
ACME (Automatic Certificate Management Environment) offers a powerful solution to these challenges. It’s an open-source protocol that automates the process of obtaining and renewing certificates, enabling a more proactive and secure approach to certificate management.
Here’s how ACME transforms certificate management:
- Automated Renewals: ACME clients automatically request new certificates before existing ones expire, eliminating the risk of manual oversight and preventing costly downtime.
- Continuous Monitoring: ACME clients continuously monitor certificate status, providing real-time visibility into potential issues and enabling proactive remediation.
- Instant Alerts: ACME systems can be configured to issue alerts when problems arise, such as impending expiration or revocation, allowing IT teams to take immediate action.
By automating these critical tasks, ACME reduces the burden on IT teams, minimizes the risk of human error, and enhances the overall security and reliability of your certificate infrastructure. It frees up valuable time and resources, allowing IT professionals to focus on strategic initiatives rather than firefighting certificate-related issues.
How ACME Works
ACME is a protocol, a set of rules for communication between an ACME client and an ACME server:
- ACME Client: This is the software that runs on your web server or application. It handles communication with the ACME server, requesting certificates and performing domain validation. Popular ACME clients include Certbot, acme.sh, and clients built into web servers like Apache and Nginx.
- ACME Server: This is the software that issues certificates. Many CAs offer ACME servers, including Let’s Encrypt, Sectigo, and GlobalSign. Leading CLM platforms like Venafi and Keyfactor also have ACME server capabilities.
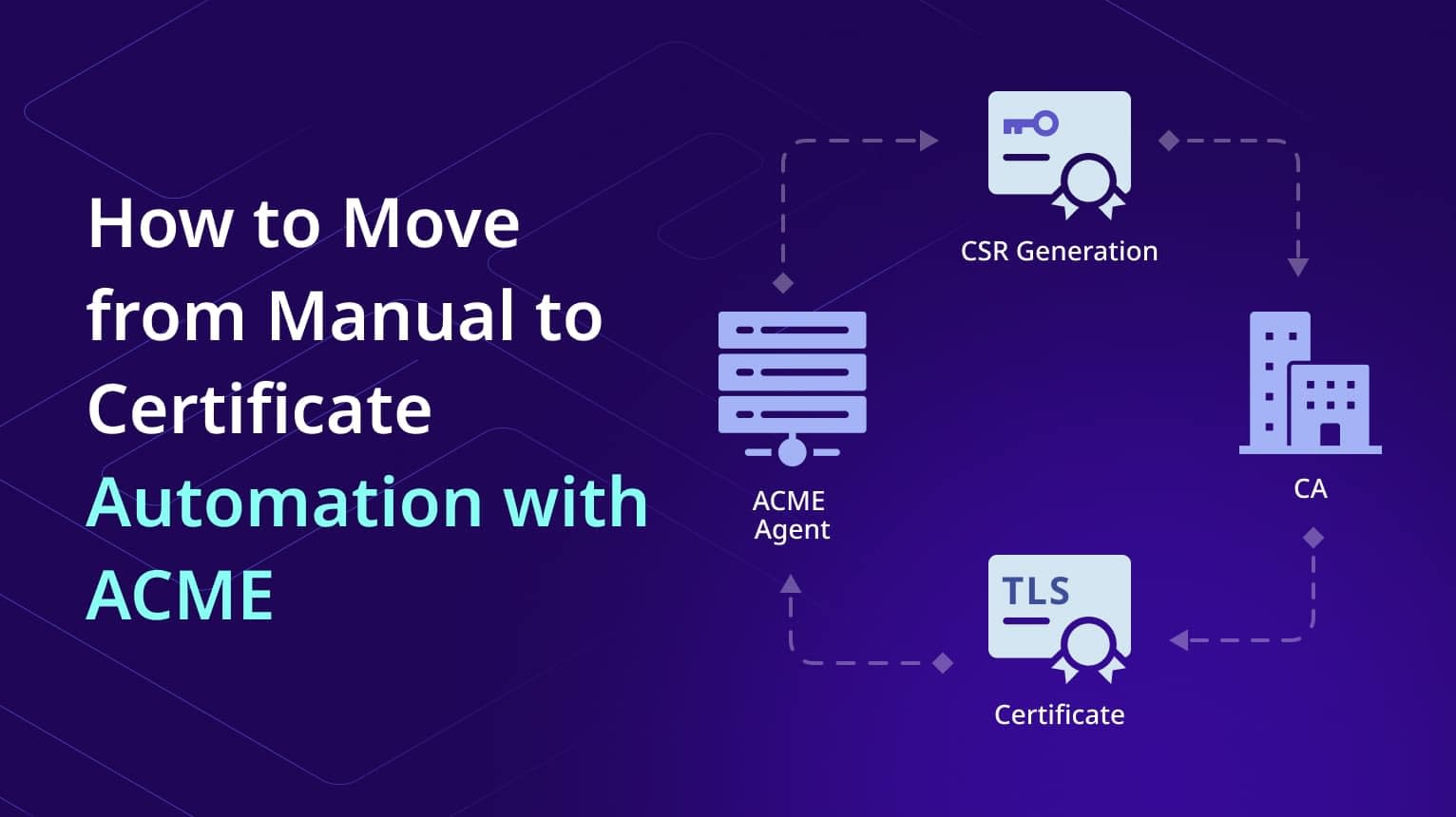
Here’s a simplified overview of the ACME process:
- Registration: The ACME client registers with the ACME server.
- Domain Validation: The ACME client proves control over the domain(s) for which it’s requesting a certificate. This is typically done through DNS validation or HTTP challenges.
- Certificate Signing Request (CSR) Generation: The ACME client generates a CSR, which contains information about the requested certificate.
- Certificate Issuance: The ACME server validates the CSR and issues the certificate.
- Certificate Installation: The ACME client installs the certificate on the web server or application.
- Renewal: The ACME client automatically renews the certificate before it expires.
Here’s How ACME Works With Other Platforms
Venafi: Venafi TLS Protect Cloud can act as an ACME server, integrating seamlessly with your existing Venafi infrastructure. This allows you to automate certificate issuance and renewal while leveraging Venafi’s advanced features like certificate discovery, inventory, and policy enforcement.
Keyfactor: Keyfactor platforms like EJBCA and Command also offer ACME server functionality. This allows you to automate certificate provisioning within your Keyfactor environment, benefiting from features like real-time monitoring, tagging, and robust auditing capabilities.
By using Venafi or Keyfactor as your ACME server, you gain the combined power of ACME automation and a comprehensive CLM platform. This provides centralized control, enhanced visibility, and streamlined workflows for managing your entire certificate lifecycle.
Key Questions to Consider Before Transitioning to ACME
Making the move to ACME requires thoughtful planning. Each organization’s environment is unique, so it’s essential to answer these key questions before diving in:
- How will ACME integrate with our existing certificates? Consider how your current certificates will transfer into an ACME-based setup. Some may need reconfiguration and understanding compatibility up front will prevent disruptions.
- Can ACME meet our compliance requirements? For industries with strict compliance standards, it’s essential that ACME automation aligns with existing security, logging, and auditing policies.
- What resources will we need to implement ACME? Transitioning to ACME can involve adjustments to existing infrastructure, setup of staging environments, and careful onboarding for the IT team. Knowing the necessary resources ahead of time will ensure a smoother transition.
Planning Your Move to ACME with a CLM Platform
Integrating ACME with your CLM platform can significantly streamline your certificate automation process. Here’s a step-by-step workflow to guide your implementation:
1. Inventory and Assessment
- Begin by conducting a comprehensive inventory of your existing certificates, including their types, expiration dates, and dependencies.
- Assess your current certificate management processes and identify areas where ACME automation can bring the most value.
2. Configure ACME Integration within your CLM
- Work with your CLM provider (e.g., Venafi, Keyfactor) to configure ACME integration. This may involve enabling the ACME server functionality within the platform and configuring any necessary settings.
- If your CLM doesn’t have a built-in ACME client, select a client that integrates well with your platform.
3. Pilot in a Staging Environment
- Before deploying ACME in production, thoroughly test your configuration in a staging environment. This allows you to validate certificate issuance, renewal, and revocation processes without risking disruption to live systems.
- Pay close attention to potential challenges like DNS configuration for domain validation and firewall rules that might interfere with ACME communication.
4. Implement Monitoring and Logging
- Configure your CLM platform and ACME client to log all certificate events. This provides an audit trail for compliance and helps with troubleshooting.
- Set up alerts for critical events like renewal failures or validation errors to ensure proactive responses and prevent potential outages.
By following this workflow and leveraging the capabilities of your CLM platform, you can effectively implement ACME automation and streamline your certificate management processes.
Automating Your Certificate Management with ACME
Transitioning to ACME-managed certificates isn’t just about automating renewals; it’s about achieving resilient, dependable certificate management. From automatic reissuance upon revocation to trust chain monitoring, ACME brings solutions to common, real-life headaches for tech teams.
But automation alone isn’t enough. Integrating protocols like ACME into existing workflows or platforms often presents challenges. Without proper planning and tailored implementation, gaps can emerge—untracked certificates, missed renewals, or disruptions in operations
Accutive Security provides the technical expertise needed to overcome these challenges. From implementation and integration to tailored automation processes and managing ongoing operations as an MSP, Accutive Security ensures your certificate management—whether using ACME or other protocols—works seamlessly within complex environments.
Moving from manual processes to ACME requires upfront planning, testing, and the right tools. But once in place, an ACME-managed setup reduces manual work, minimizes the risk of missed renewals, and gives you peace of mind that certificates are continuously monitored and maintained.











Comment