ADM
Data Masking & Anonymization Tool
Discover, mask, and anonymize sensitive data across SQL Server, Oracle, and more — fast, secure, and compliant with GDPR, HIPAA, and CCPA.

Discover, mask, and anonymize sensitive data across SQL Server, Oracle, and more — fast, secure, and compliant with GDPR, HIPAA, and CCPA.



in Cost Savings
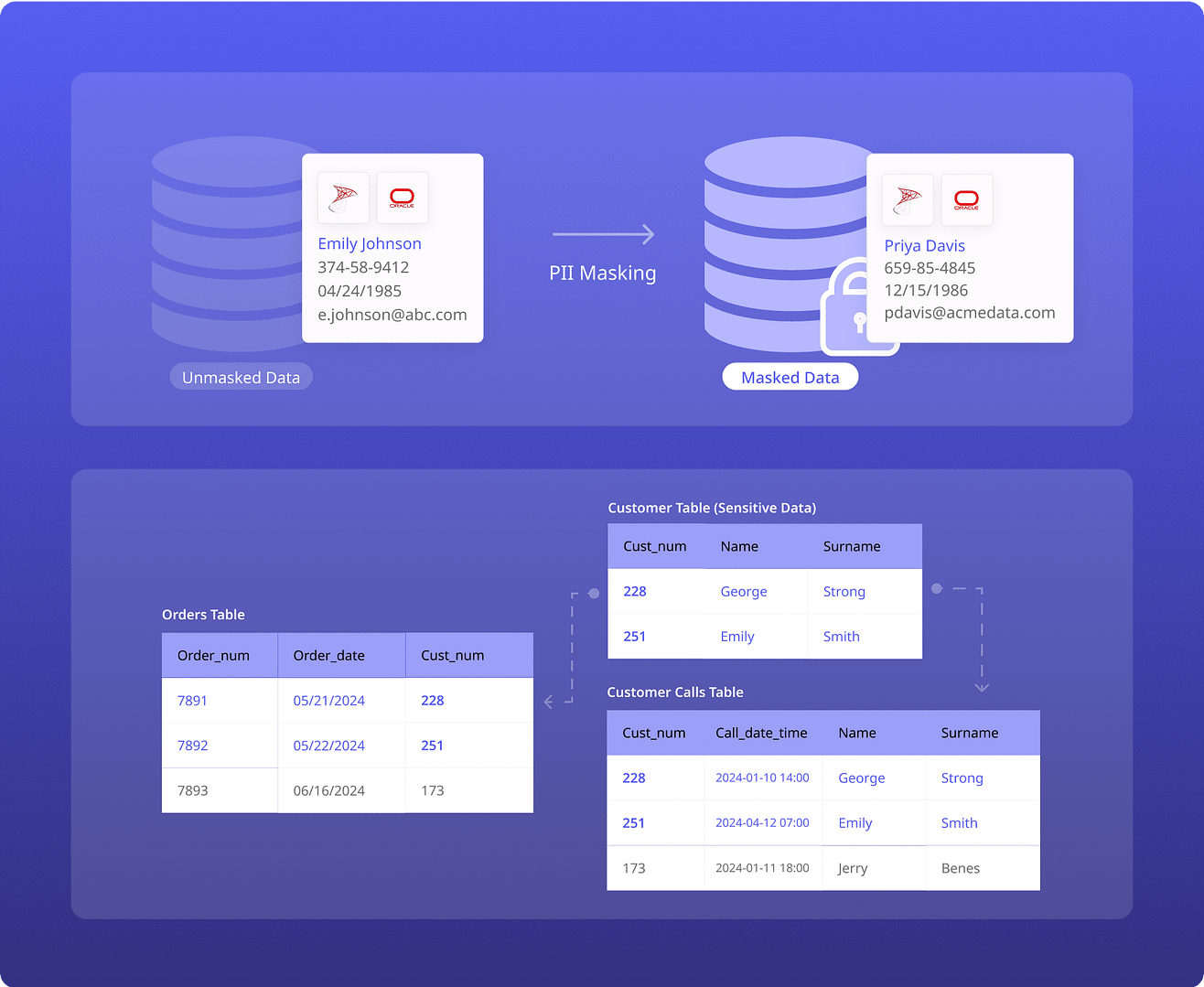
Securely mask sensitive data at rest, creating secure, realistic copies for non-production use, like testing, development and analytics, without exposing personally identifiable information (PII).
Automatically identify and protect sensitive data to meet privacy regulations (e.g., GDPR, CCPA, PIPEDA) and reduce your risk of breaches, keeping your organization compliant and secure.
Generate and manage high-quality test data that maintains data integrity and realism, enabling reliable, compliant testing without compromising data security.
Provide DevOps teams with access to safe, masked data, enabling faster development and testing cycles, so you can innovate securely and meet release deadlines.
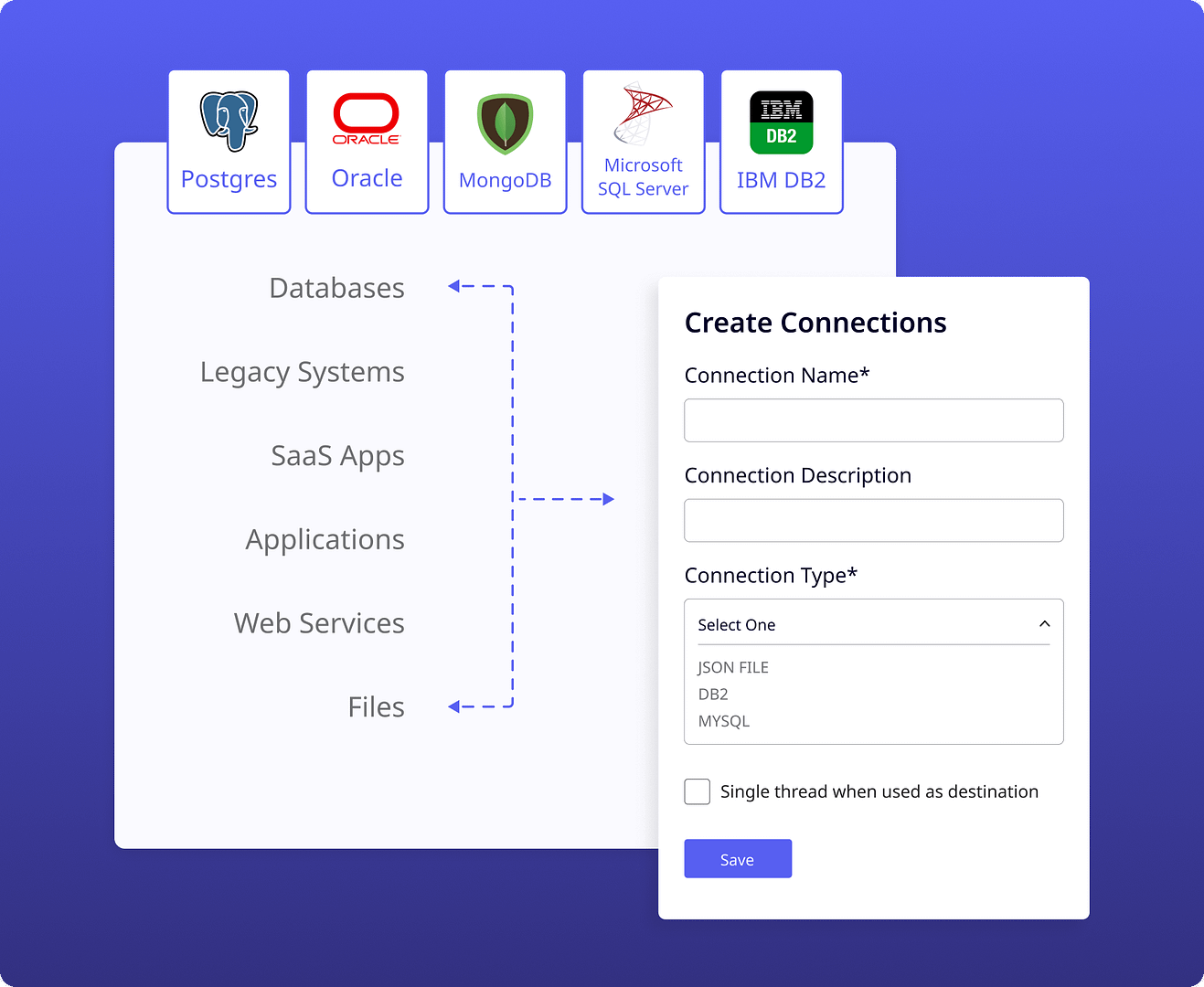
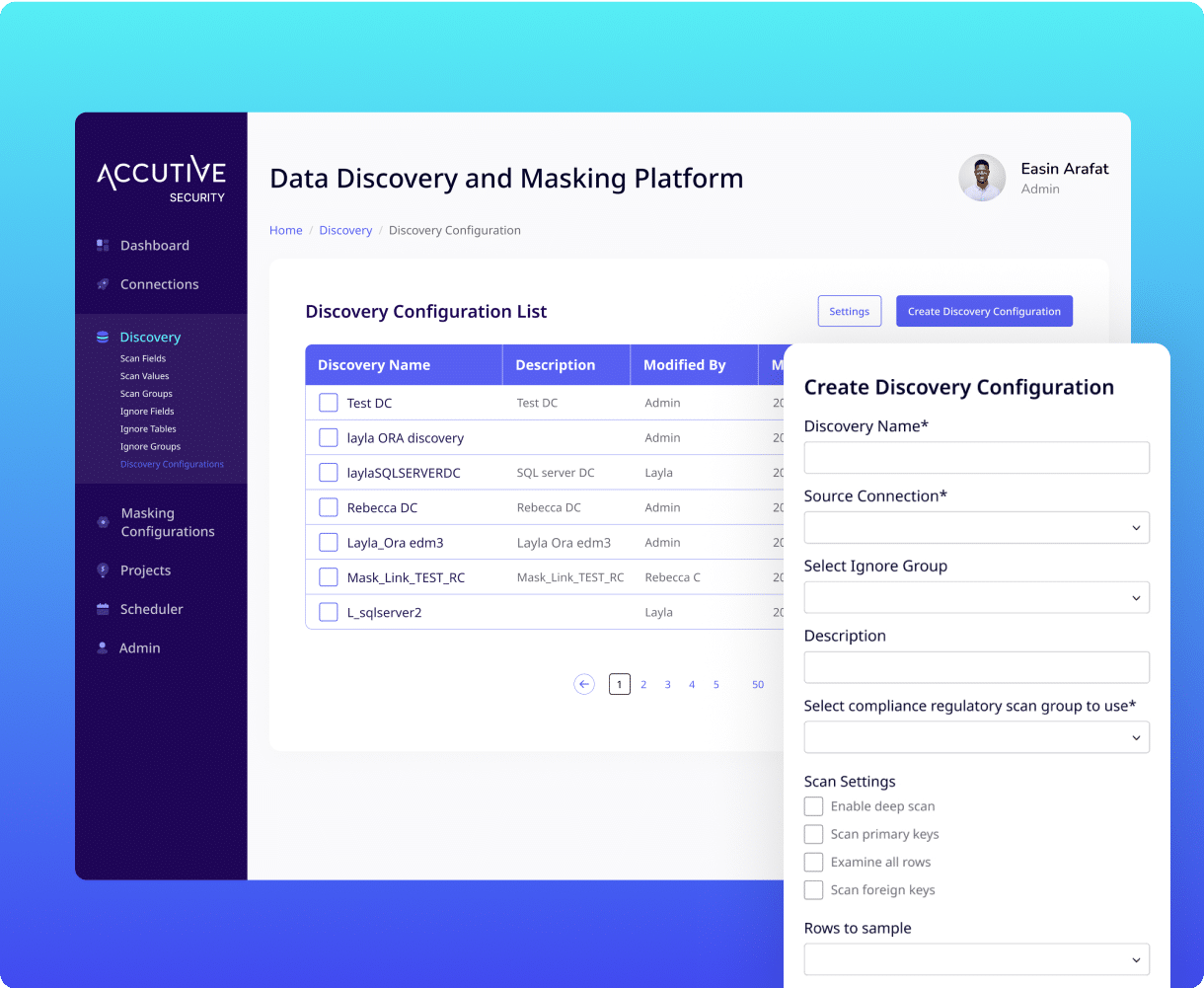
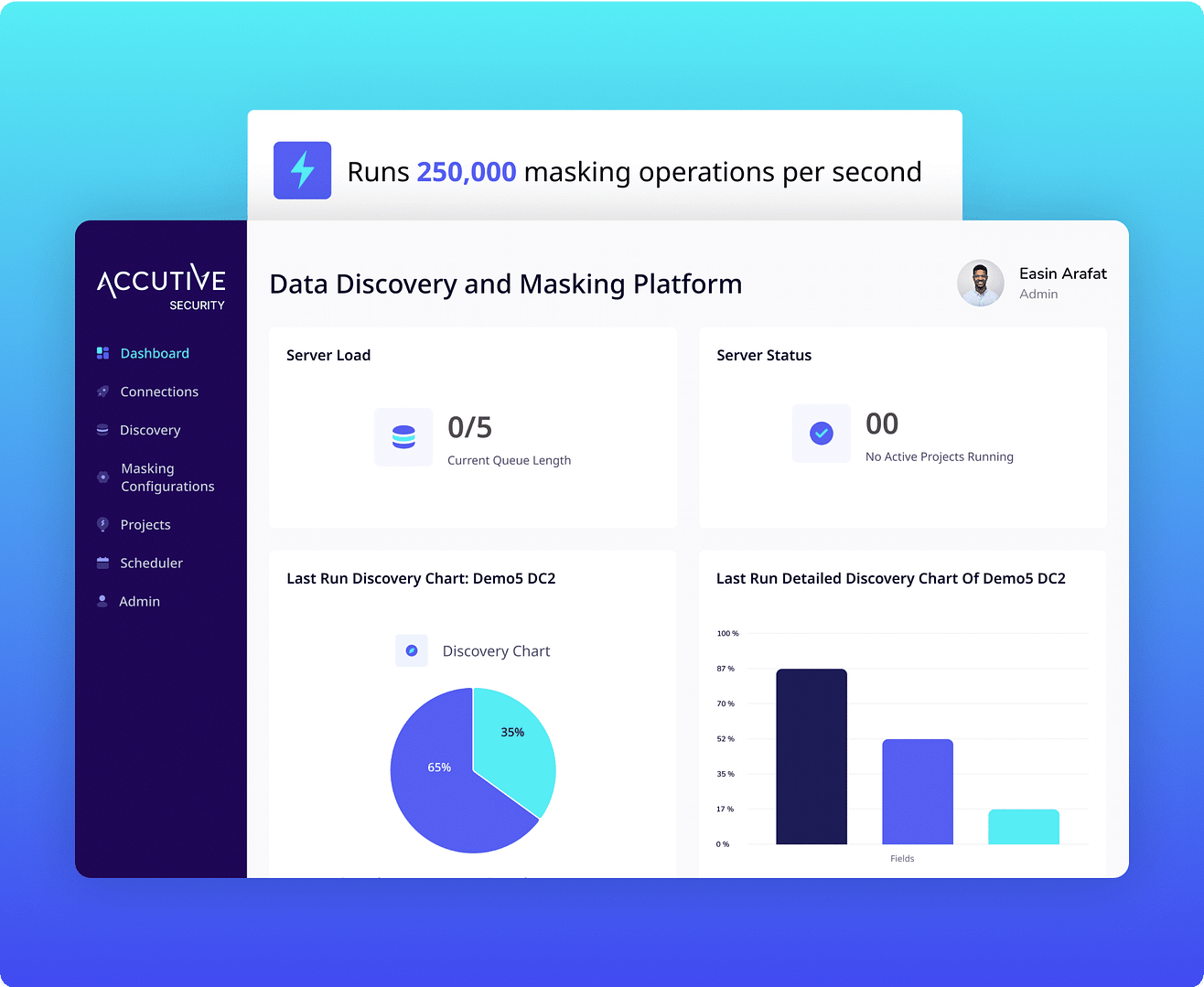

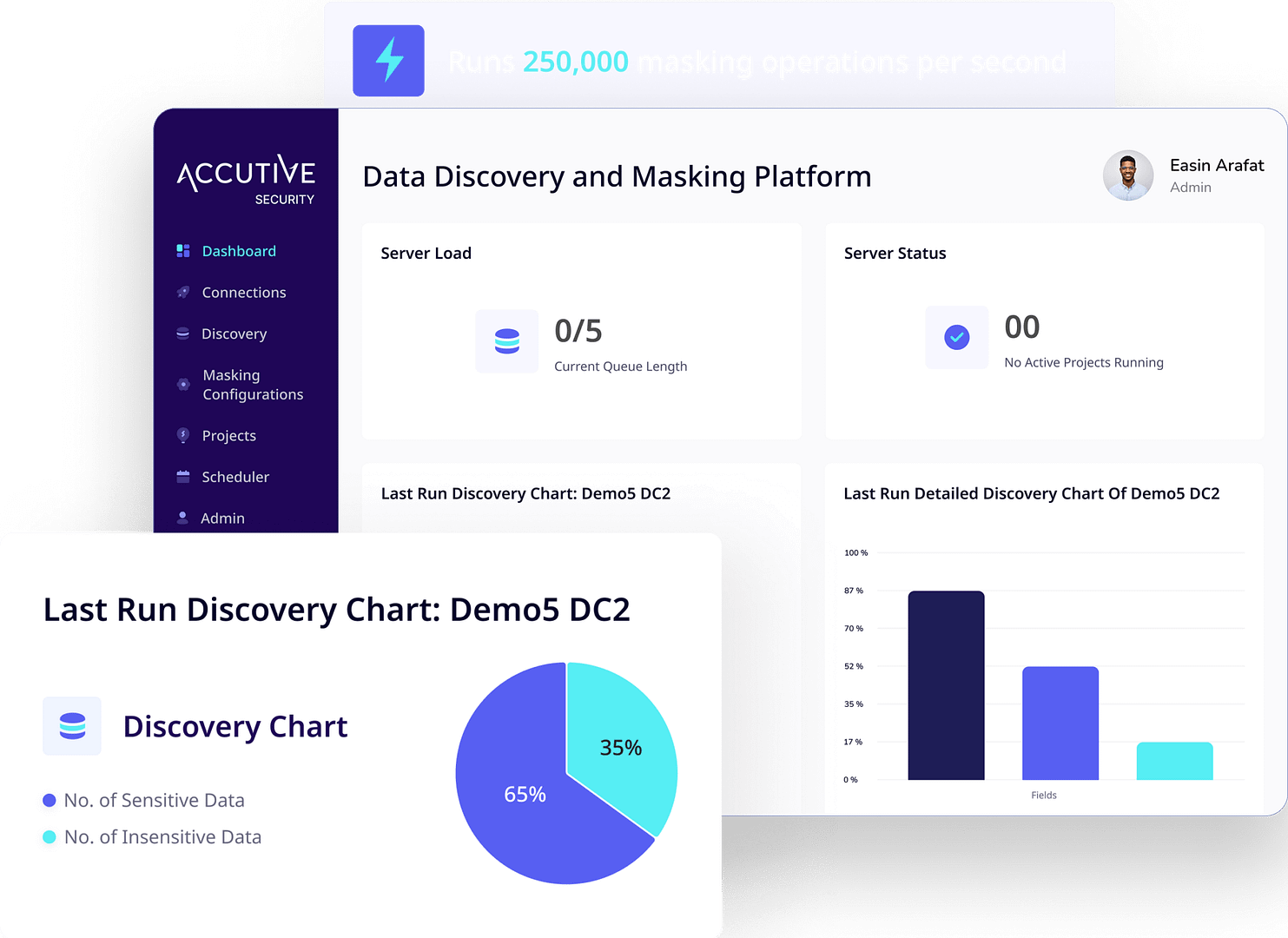
ADM enables fast, format-preserving data masking across complex database systems, including SQL Server, Oracle, PostgreSQL, and more—preserving referential integrity and maintaining schema structure while ensuring privacy compliance. It supports test, QA, and CI/CD environments, masking millions of rows in minutes with performance exceeding 250,000 operations per second.
ADM transforms sensitive data into anonymized, realistic records using format-preserving anonymization—ensuring no exposure of real PII while remaining fully compatible with data privacy laws like GDPR and HIPAA. It’s ideal for testing, analytics, or secure collaboration, with built-in audit logging to support compliance requirements.

Discover a Test Data Management Platform
Achieve airtight GDPR, CCPA, and HIPAA compliance with audit-ready reporting and no blind spots


Intuitive masking tools boost testing accuracy and maintain data usability – no need for manual scripts or complex workarounds
Lower risks and save time by automating data protection, reducing resource strain, and enhancing audit preparedness


Enable test and QA teams with fully protected, masked production data securing sensitive information, ensuring compliance and accelerating results.
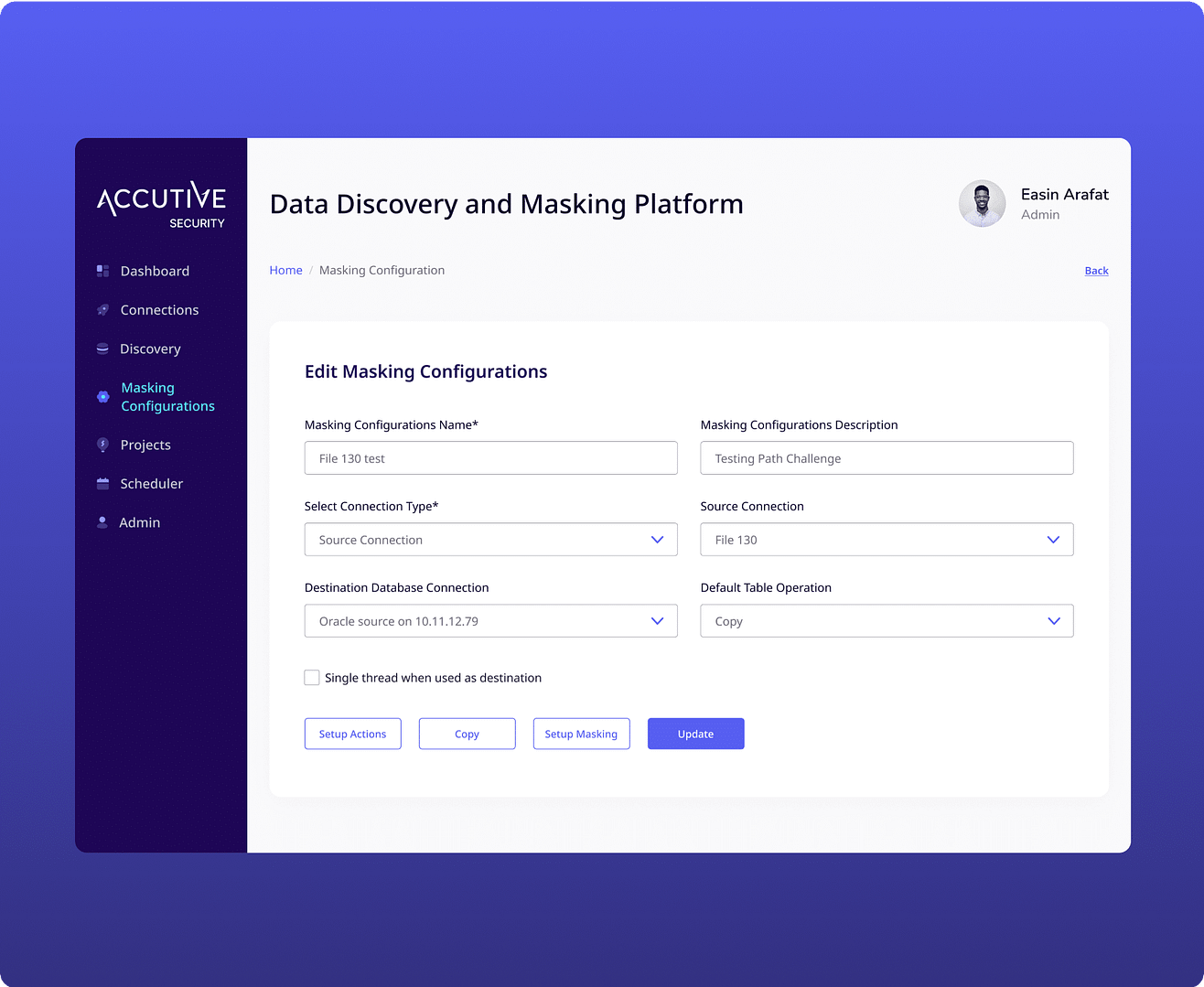
Analyze databases to find sensitive data everywhere and anywhere in your network enabling testing and facilitating analytics while ensuring compliance.
Identify and select just right data sets from large production databases for rapid, accurate testing or analytics while reducing storage costs and processing time.

Automate data discovery, subset and masking processes empowering technical teams with the right data while preserving security and compliance.
Substitute your critical sensitive data with a non-sensitive placeholder for secure usage + sharing.
with our simple 4-step process



ADM Solves Complex Masking Challenges
Universal and User-Friendly data masking with ADM: Effortlessly Identify and Mask Sensitive Data Across All Your Databases and Files
Robust Database Masking for Security and Compliance
Preserve important data characteristics so that your data remains functional but still anonymized.
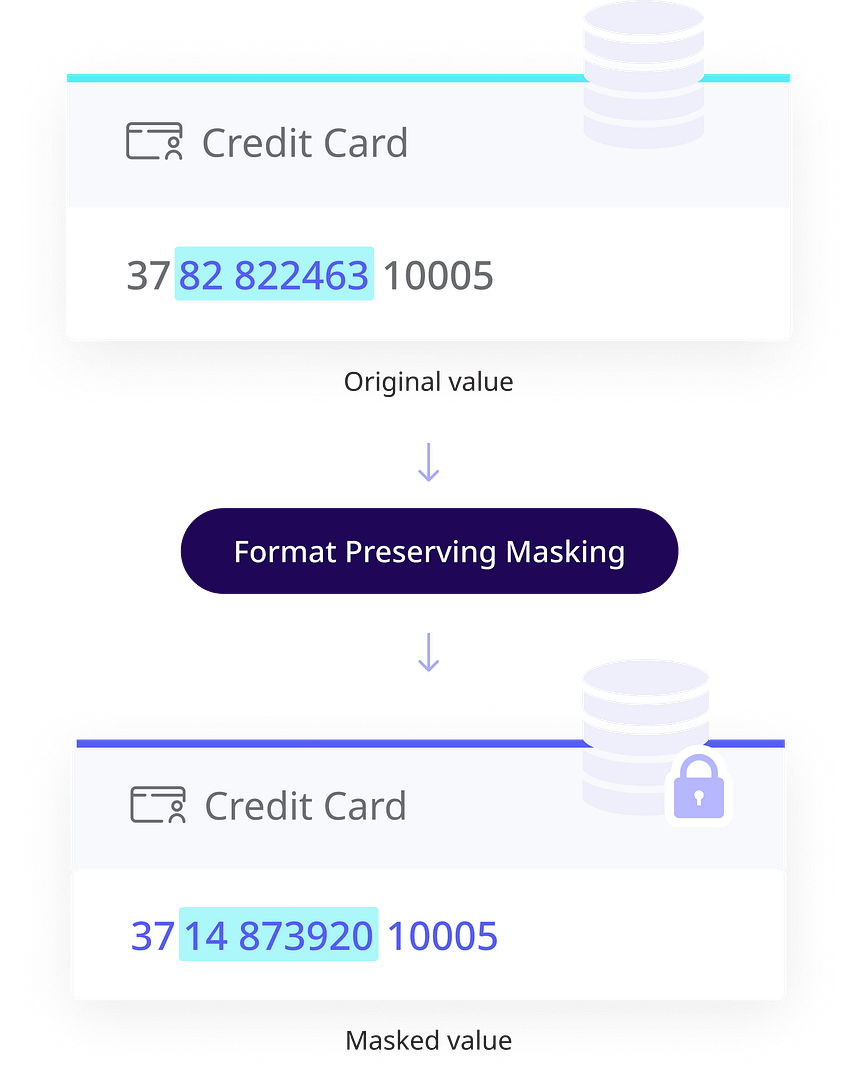
Example : Format-Preserving Masking retains data structures, such as the American Express card format shown in the graphic, for system validation without revealing card details.
Example : An SSN appearing in multiple databases, e.g. 109-98-1767 (fictitious but adheres to the standard—109 shows it was issued in NY), can be consistently masked as 109-00-5874 across all other databases, files, and more.

Answers to Your Data Security and Compliance Questions
Used by teams handling millions of records to meet HIPAA, GDPR, and SOC 2 standards—without risking a single leak.